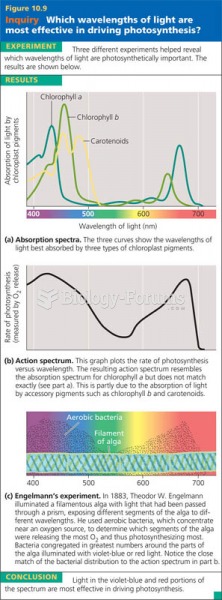
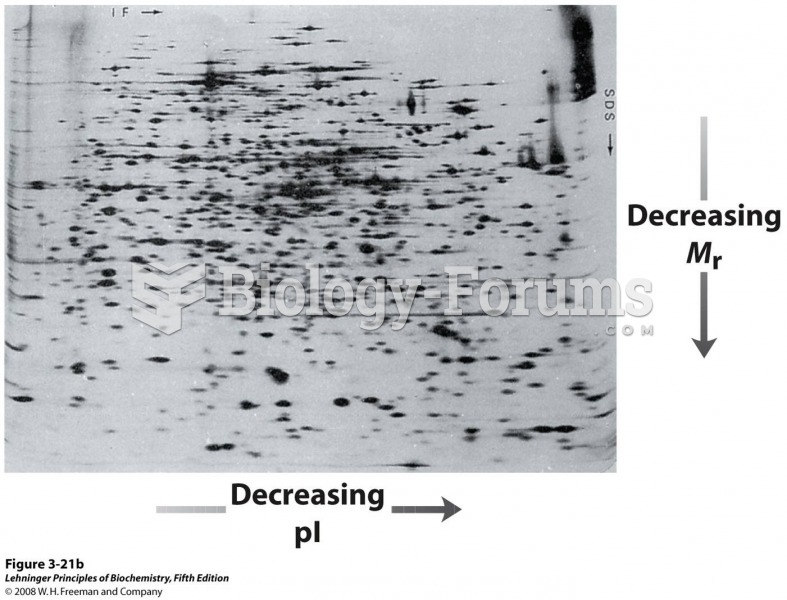
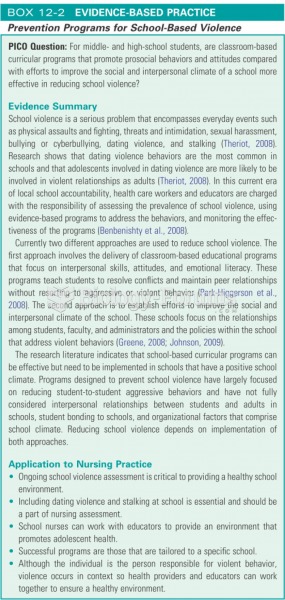
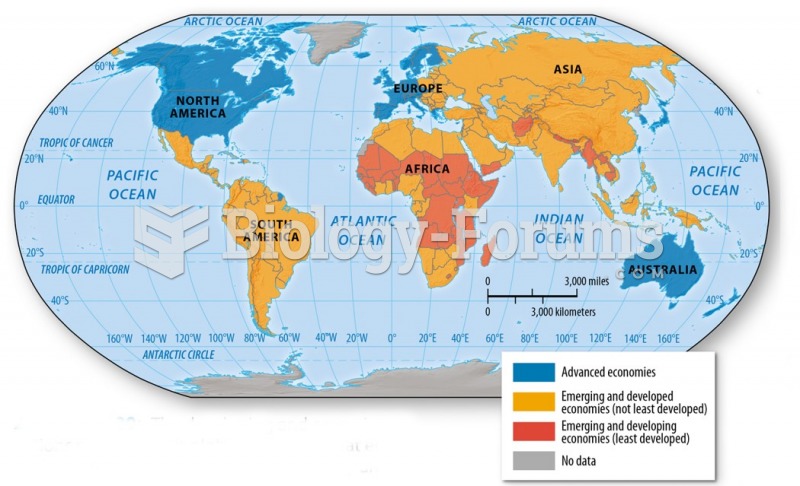
|
|
|
Methicillin-resistant Staphylococcus aureus or MRSA was discovered in 1961 in the United Kingdom. It if often referred to as a superbug. MRSA infections cause more deaths in the United States every year than AIDS.
Nearly all drugs pass into human breast milk. How often a drug is taken influences the amount of drug that will pass into the milk. Medications taken 30 to 60 minutes before breastfeeding are likely to be at peak blood levels when the baby is nursing.
More than 150,000 Americans killed by cardiovascular disease are younger than the age of 65 years.
There are major differences in the metabolism of morphine and the illegal drug heroin. Morphine mostly produces its CNS effects through m-receptors, and at k- and d-receptors. Heroin has a slight affinity for opiate receptors. Most of its actions are due to metabolism to active metabolites (6-acetylmorphine, morphine, and morphine-6-glucuronide).
Earwax has antimicrobial properties that reduce the viability of bacteria and fungus in the human ear.