|
|
|
Though methadone is often used to treat dependency on other opioids, the drug itself can be abused. Crushing or snorting methadone can achieve the opiate "rush" desired by addicts. Improper use such as these can lead to a dangerous dependency on methadone. This drug now accounts for nearly one-third of opioid-related deaths.
Prostaglandins were first isolated from human semen in Sweden in the 1930s. They were so named because the researcher thought that they came from the prostate gland. In fact, prostaglandins exist and are synthesized in almost every cell of the body.
The modern decimal position system was the invention of the Hindus (around 800 AD), involving the placing of numerals to indicate their value (units, tens, hundreds, and so on).
In inpatient settings, adverse drug events account for an estimated one in three of all hospital adverse events. They affect approximately 2 million hospital stays every year, and prolong hospital stays by between one and five days.
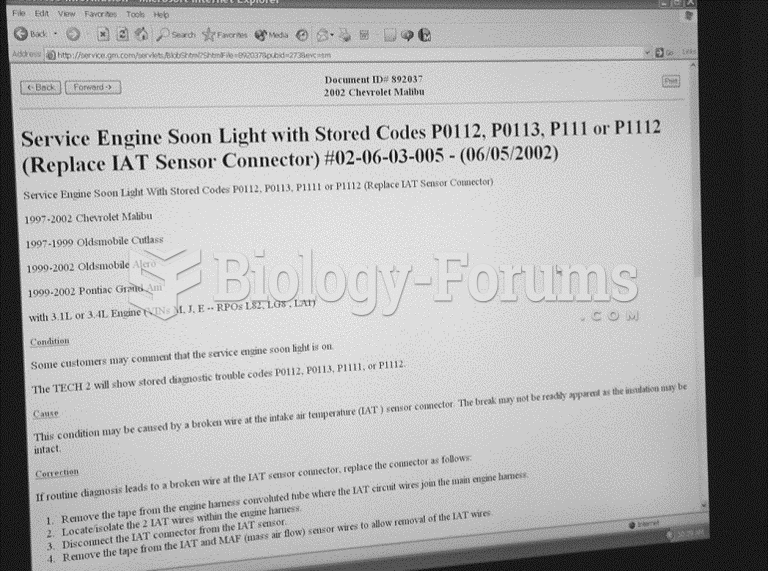
Computer programs are available that crosscheck a new drug's possible trade name with all other trade names currently available. These programs detect dangerous similarities between names and alert the manufacturer of the drug.