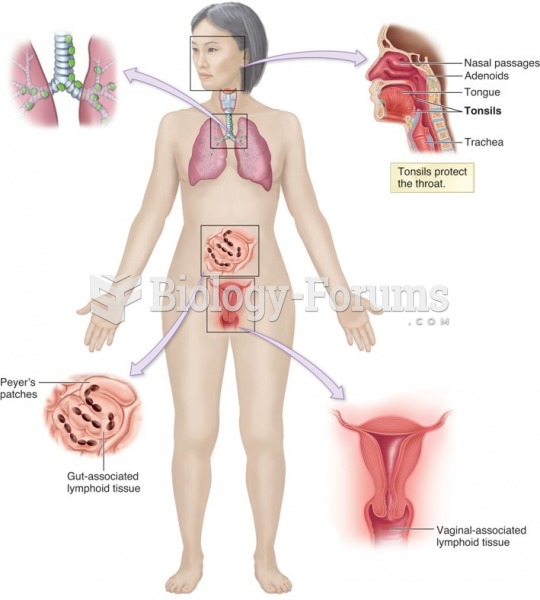
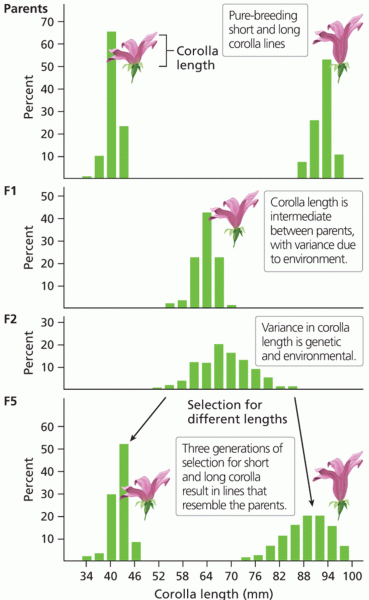
|
|
|
Since 1988, the CDC has reported a 99% reduction in bacterial meningitis caused by Haemophilus influenzae, due to the introduction of the vaccine against it.
In 1835 it was discovered that a disease of silkworms known as muscardine could be transferred from one silkworm to another, and was caused by a fungus.
The human body's pharmacokinetics are quite varied. Our hair holds onto drugs longer than our urine, blood, or saliva. For example, alcohol can be detected in the hair for up to 90 days after it was consumed. The same is true for marijuana, cocaine, ecstasy, heroin, methamphetamine, and nicotine.
Only 12 hours after an egg cell is fertilized by a sperm cell, the egg cell starts to divide. As it continues to divide, it moves along the fallopian tube toward the uterus at about 1 inch per day.
Thyroid conditions cause a higher risk of fibromyalgia and chronic fatigue syndrome.
 (a) The Dmanisi cranium (right) shows similarities to early African H. erectus including the Narioko
(a) The Dmanisi cranium (right) shows similarities to early African H. erectus including the Narioko
 The philosophical journey requires self-examination. Your responsibility as a critical thinker is to
The philosophical journey requires self-examination. Your responsibility as a critical thinker is to