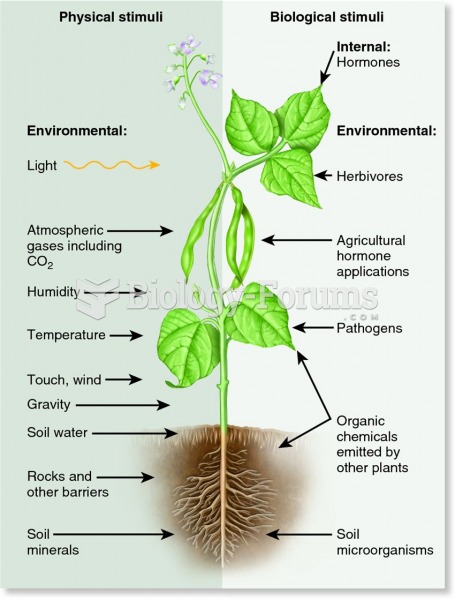
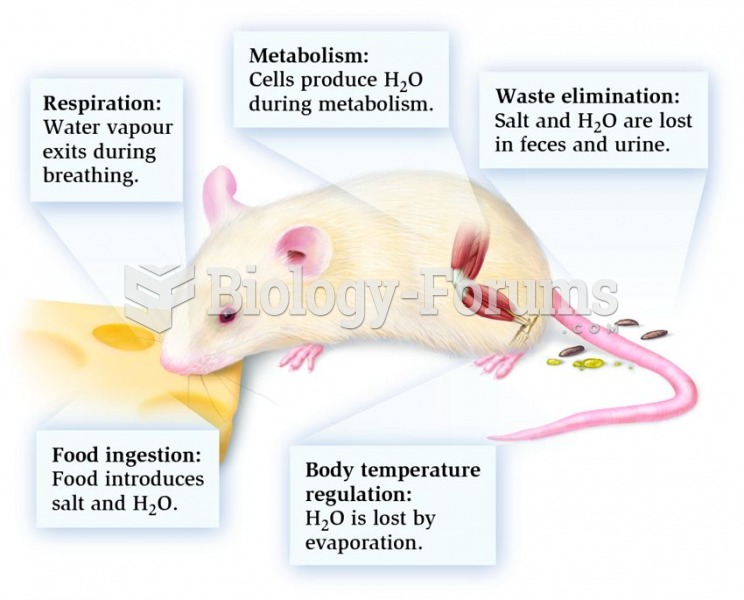
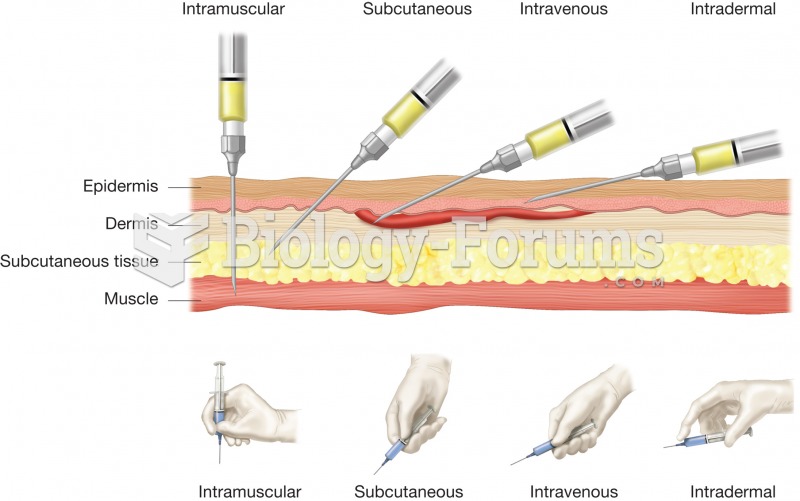
|
|
|
The most dangerous mercury compound, dimethyl mercury, is so toxic that even a few microliters spilled on the skin can cause death. Mercury has been shown to accumulate in higher amounts in the following types of fish than other types: swordfish, shark, mackerel, tilefish, crab, and tuna.
Atropine was named after the Greek goddess Atropos, the oldest and ugliest of the three sisters known as the Fates, who controlled the destiny of men.
The highest suicide rate in the United States is among people ages 65 years and older. Almost 15% of people in this age group commit suicide every year.
The cure for trichomoniasis is easy as long as the patient does not drink alcoholic beverages for 24 hours. Just a single dose of medication is needed to rid the body of the disease. However, without proper precautions, an individual may contract the disease repeatedly. In fact, most people develop trichomoniasis again within three months of their last treatment.
The human body's pharmacokinetics are quite varied. Our hair holds onto drugs longer than our urine, blood, or saliva. For example, alcohol can be detected in the hair for up to 90 days after it was consumed. The same is true for marijuana, cocaine, ecstasy, heroin, methamphetamine, and nicotine.