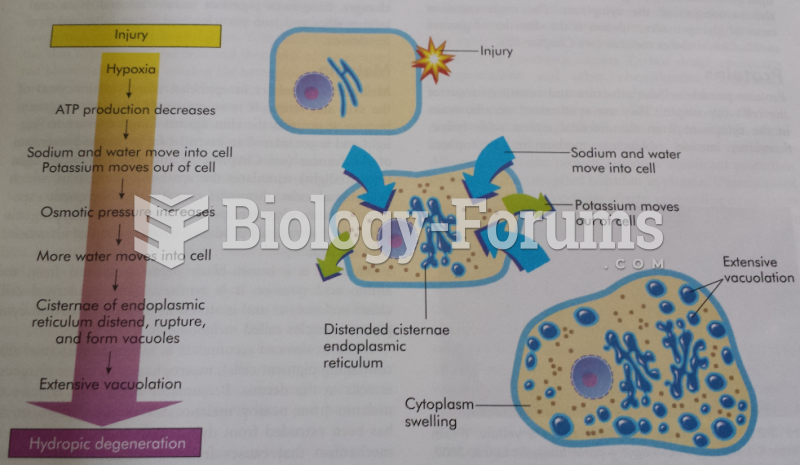
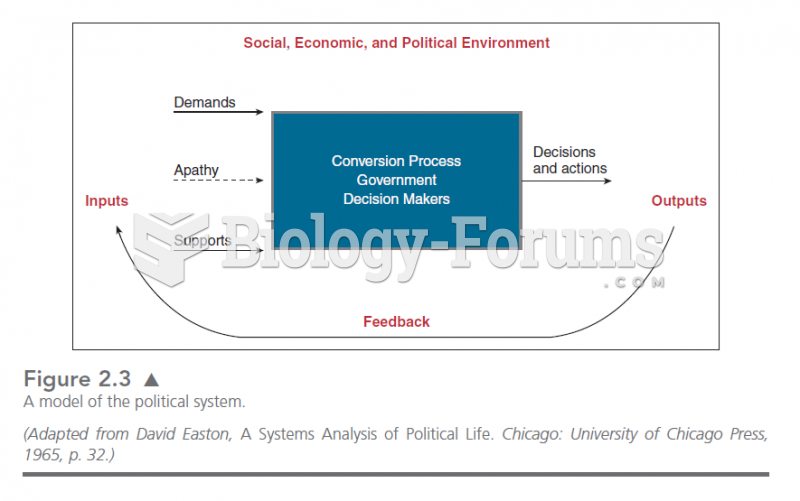
|
|
|
In ancient Rome, many of the richer people in the population had lead-induced gout. The reason for this is unclear. Lead poisoning has also been linked to madness.
Studies show that systolic blood pressure can be significantly lowered by taking statins. In fact, the higher the patient's baseline blood pressure, the greater the effect of statins on his or her blood pressure.
According to the Migraine Research Foundation, migraines are the third most prevalent illness in the world. Women are most affected (18%), followed by children of both sexes (10%), and men (6%).
Blood in the urine can be a sign of a kidney stone, glomerulonephritis, or other kidney problems.
There used to be a metric calendar, as well as metric clocks. The metric calendar, or "French Republican Calendar" divided the year into 12 months, but each month was divided into three 10-day weeks. Each day had 10 decimal hours. Each hour had 100 decimal minutes. Due to lack of popularity, the metric clocks and calendars were ended in 1795, three years after they had been first marketed.