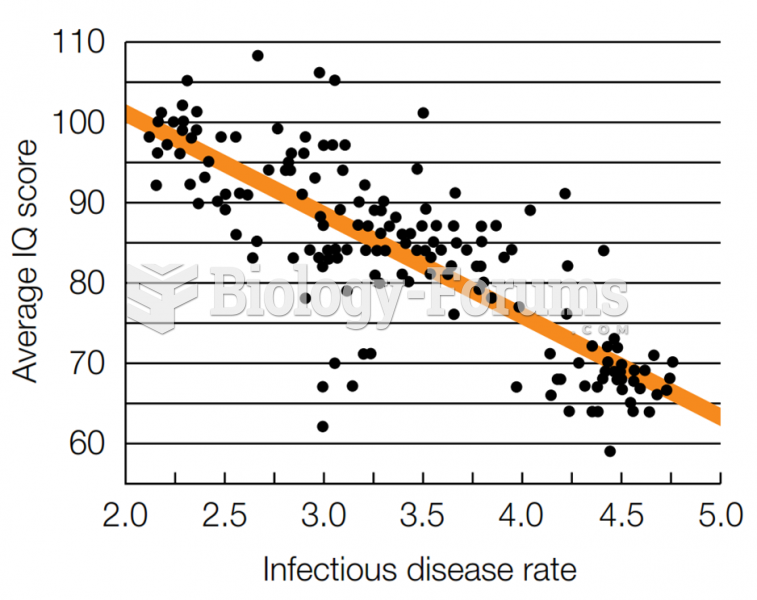
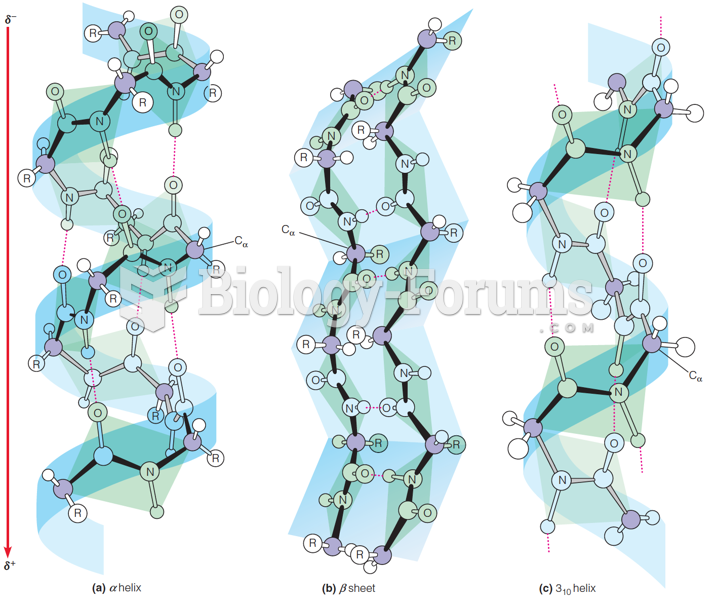
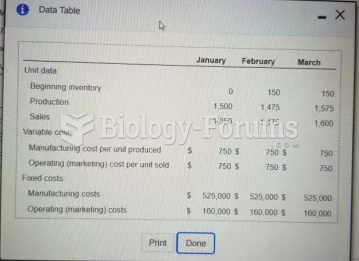
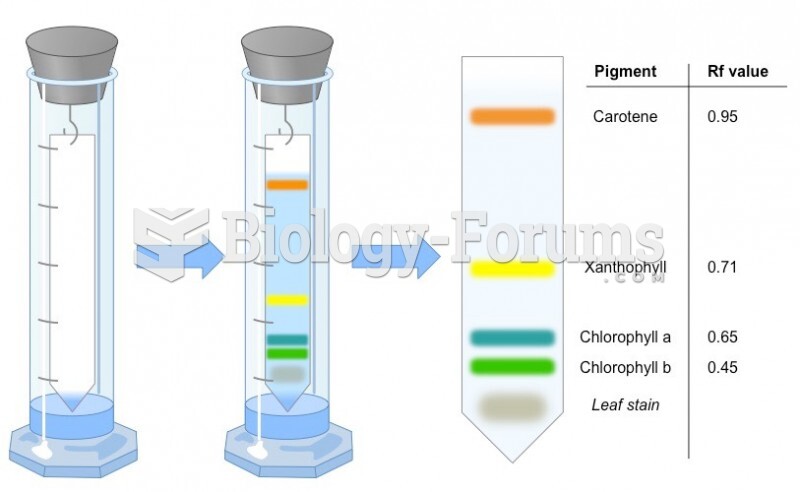
Answer to Question 1
Describe EFT and explain the various ways funds are transferred.
Electronic funds transfer (EFT) is an electronic delivery system for financial transactions. With the use of computers, financial institutions can perform numerous banking transactions without the use of checks. Advantages include no lost or stolen checks and payments are made quickly and on time.
Automated teller machines (ATMS). Automated teller machines (ATMs), located at banks, in shopping malls, in supermarkets, and many other places, enable customers to obtain cash and make deposits. When a customer activates an automated teller machine with an EFT card and enters a personal identification number (PIN) or a secret password, the computer is ready.
Debit Card. Another way funds are electronically transferred is by using a debit card. Debit cards are used in the place of checks. Debit cards are obtained through the bank by completing a credit application for a debit card through companies such as VISA or MasterCard. Once the application is approved, the bank issues the debit card, which can be used either as a debit card or a credit card. When using a debit card, a secret password must be entered and then the money is taken directly from the individual's or company's checking account. The only drawback is if the card is lost, it can still be used as a credit card.
Direct Payroll Deposit. Direct payroll deposit enables an organization to pay its employees without writing checks. Instead, the organization furnishes the bank with a magnetic tape with a description of all payroll disbursements to be made to the employees. The bank credits the account of each of the employees with his or her net pay and withdraws the amount from the account of the employer making payment.
Automatic Deposits. Funds can be automatically deposited as well. The company making the automatic deposit must be given the account's American Banking Association (ABA) electronic routing number and the account number in which the money is to be deposited. This routing number and bank account number is usually printed on the bottom of all checks.
Automatic Debits. Automatic debits are preauthorized automated transfer of funds for a company from one account to another within the same financial institution.
Web Banking. Most banks offer business banking, investing, and insurance facilities to their customers on the Internet. Web banking provides easy management of banking transactions online wherever you have access to the Internet. Primary functions of such services enable business customers to make electronic transfers between accounts and get real-time information on balances and transactions. Accounts may be viewed and manipulated on screen just as you might with more traditional methods of banking.
Telephone Transfers. Some companies allow payments to be made by phone. Telephone transfers can be made by calling the company to whom you wish to make payment, writing a check, giving them the check number and amount, and the company will draft the amount from your checking account and the bank will honor the check.
Answer to Question 2
Describe at least two ethical issues regarding e-mail. Include in your response the impact from a supervisor's point of view as well as from the employee's point of view.
Answers will vary; however, students' responses should include reasons why employers have legitimate reasons for monitoring their employees' computer use. From an employee's point of view, students' responses should include issues such as their privacy and their concern for being monitored during their lunch break (although they are using the organization's resources).