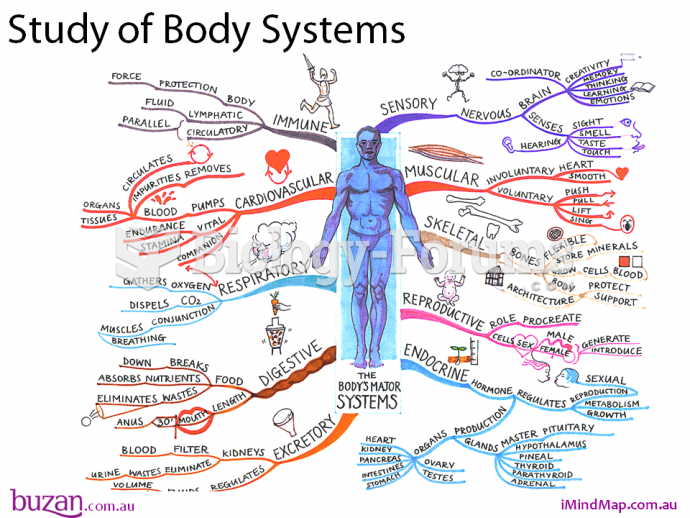
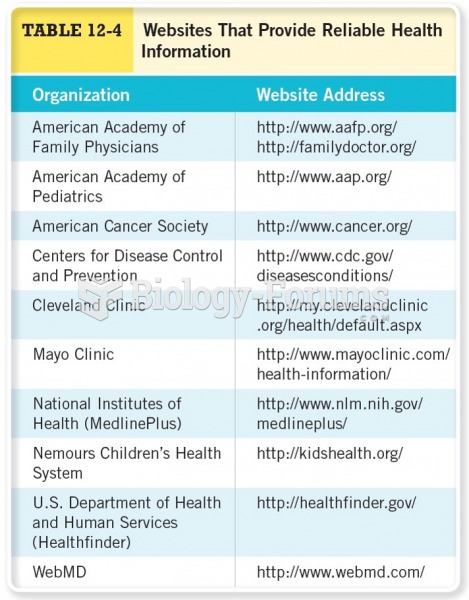
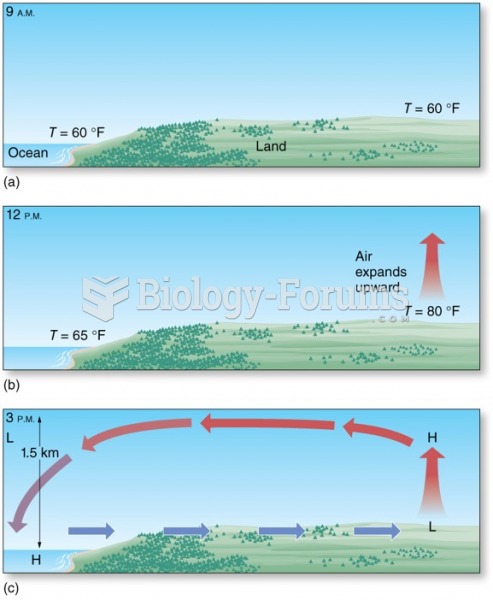
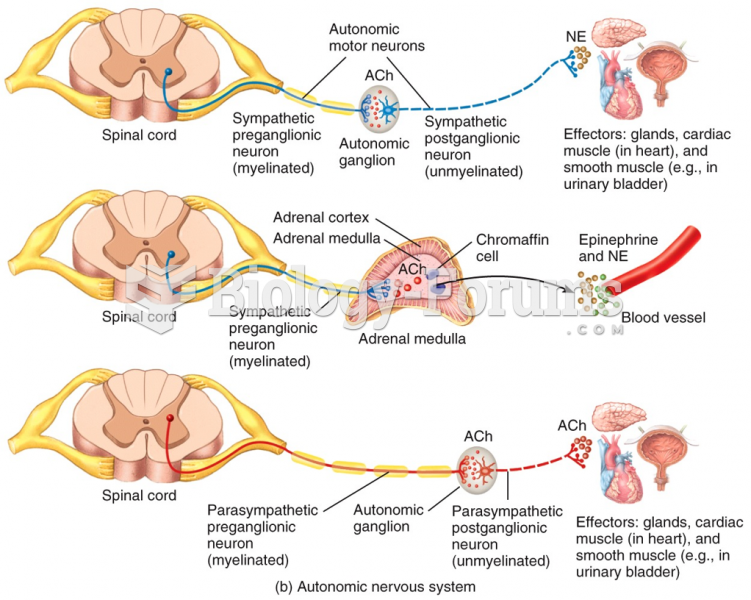
|
|
|
Did you know?
More than 4.4billion prescriptions were dispensed within the United States in 2016.
Did you know?
Atropine, along with scopolamine and hyoscyamine, is found in the Datura stramonium plant, which gives hallucinogenic effects and is also known as locoweed.
Did you know?
Amphetamine poisoning can cause intravascular coagulation, circulatory collapse, rhabdomyolysis, ischemic colitis, acute psychosis, hyperthermia, respiratory distress syndrome, and pericarditis.
Did you know?
There are more sensory neurons in the tongue than in any other part of the body.
Did you know?
The word drug comes from the Dutch word droog (meaning "dry"). For centuries, most drugs came from dried plants, hence the name.