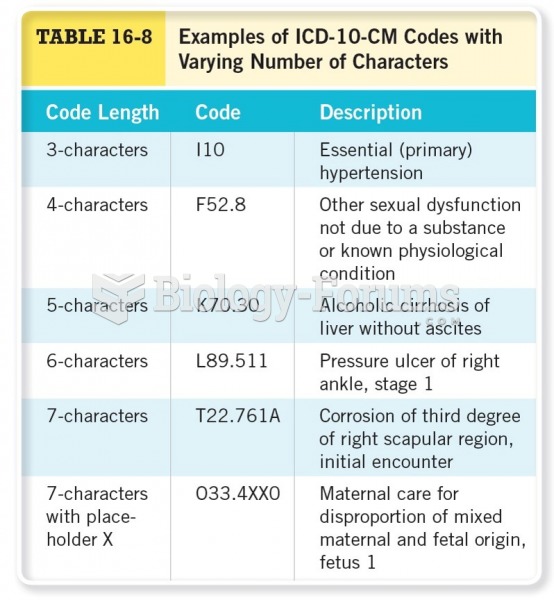
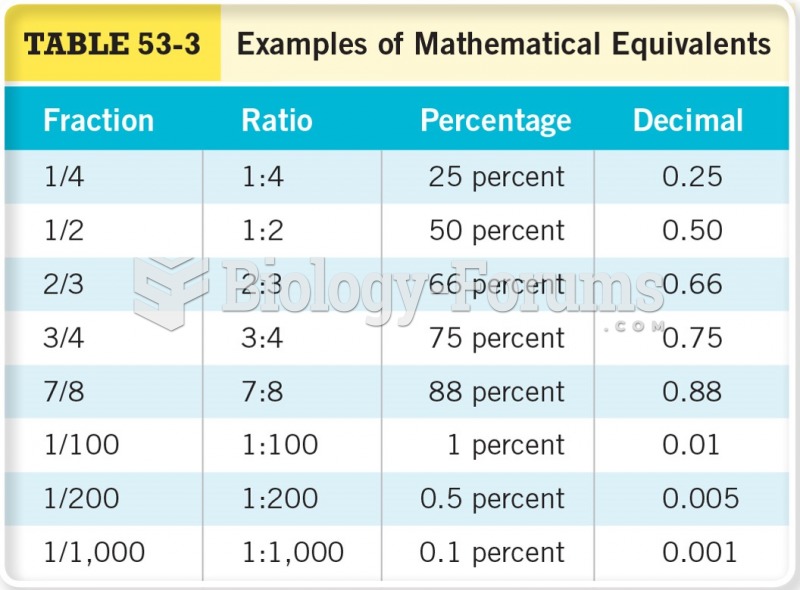
This topic contains a solution. Click here to go to the answer
|
|
|
Did you know?
There are more sensory neurons in the tongue than in any other part of the body.
Did you know?
About 3.2 billion people, nearly half the world population, are at risk for malaria. In 2015, there are about 214 million malaria cases and an estimated 438,000 malaria deaths.
Did you know?
The ratio of hydrogen atoms to oxygen in water (H2O) is 2:1.
Did you know?
Street names for barbiturates include reds, red devils, yellow jackets, blue heavens, Christmas trees, and rainbows. They are commonly referred to as downers.
Did you know?
Vaccines prevent between 2.5 and 4 million deaths every year.