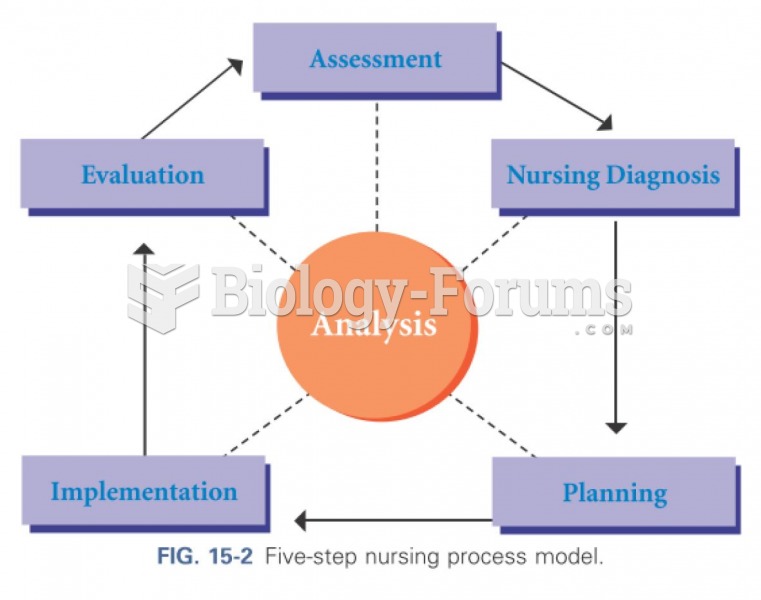
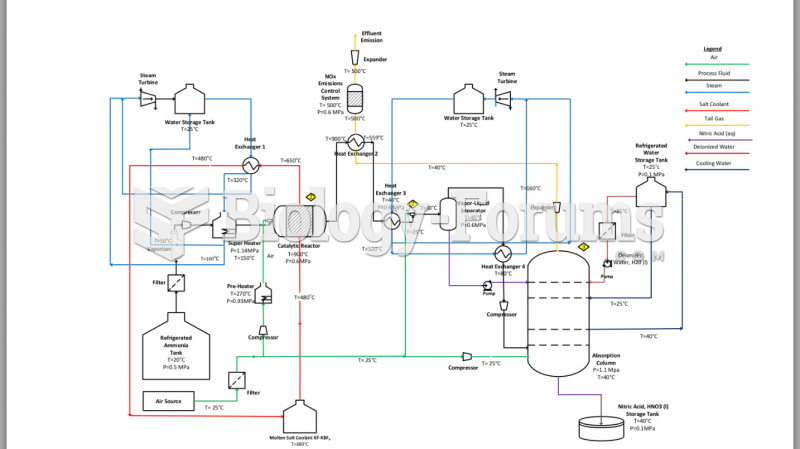
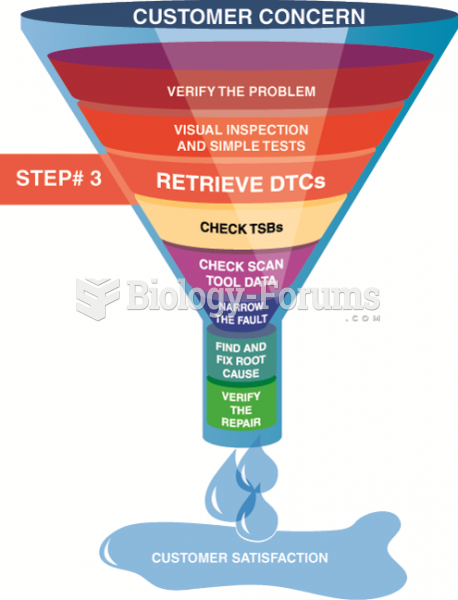
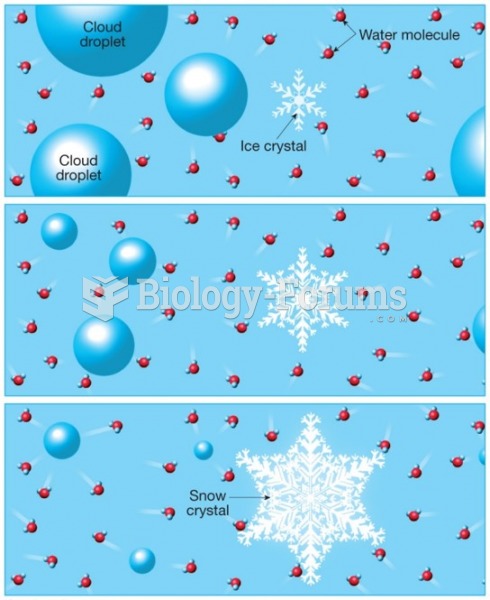
|
|
|
The use of salicylates dates back 2,500 years to Hippocrates’s recommendation of willow bark (from which a salicylate is derived) as an aid to the pains of childbirth. However, overdosage of salicylates can harm body fluids, electrolytes, the CNS, the GI tract, the ears, the lungs, the blood, the liver, and the kidneys and cause coma or death.
Many of the drugs used by neuroscientists are derived from toxic plants and venomous animals (such as snakes, spiders, snails, and puffer fish).
The newest statin drug, rosuvastatin, has been called a superstatin because it appears to reduce LDL cholesterol to a greater degree than the other approved statin drugs.
Studies show that systolic blood pressure can be significantly lowered by taking statins. In fact, the higher the patient's baseline blood pressure, the greater the effect of statins on his or her blood pressure.
Never take aspirin without food because it is likely to irritate your stomach. Never give aspirin to children under age 12. Overdoses of aspirin have the potential to cause deafness.