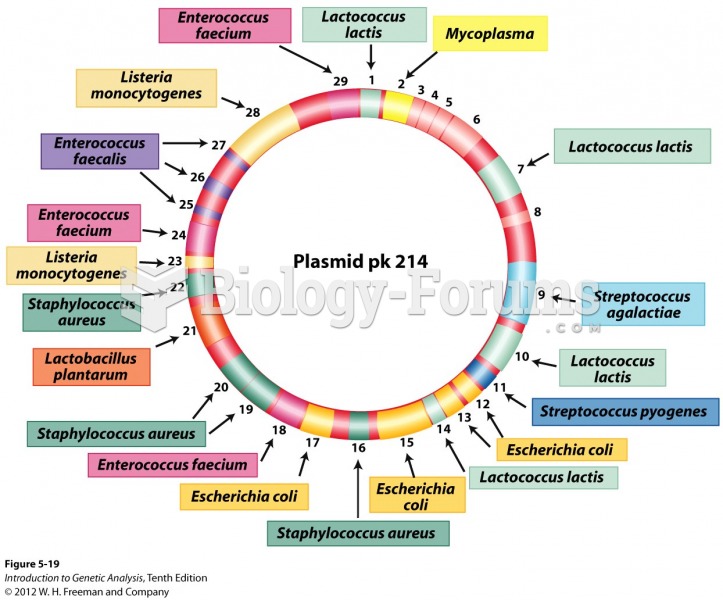
|
|
|
There are 60,000 miles of blood vessels in every adult human.
Signs of depression include feeling sad most of the time for 2 weeks or longer; loss of interest in things normally enjoyed; lack of energy; sleep and appetite disturbances; weight changes; feelings of hopelessness, helplessness, or worthlessness; an inability to make decisions; and thoughts of death and suicide.
As the western states of America were settled, pioneers often had to drink rancid water from ponds and other sources. This often resulted in chronic diarrhea, causing many cases of dehydration and death that could have been avoided if clean water had been available.
On average, someone in the United States has a stroke about every 40 seconds. This is about 795,000 people per year.
When intravenous medications are involved in adverse drug events, their harmful effects may occur more rapidly, and be more severe than errors with oral medications. This is due to the direct administration into the bloodstream.