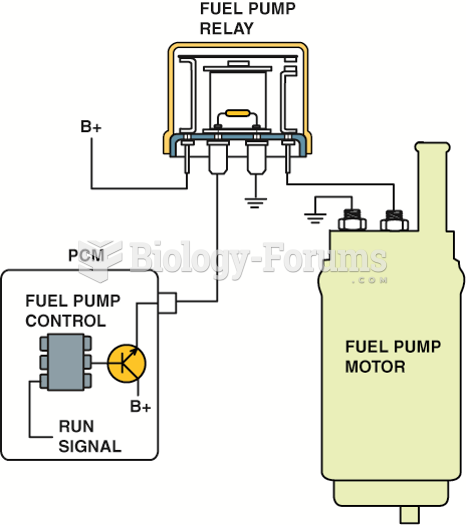
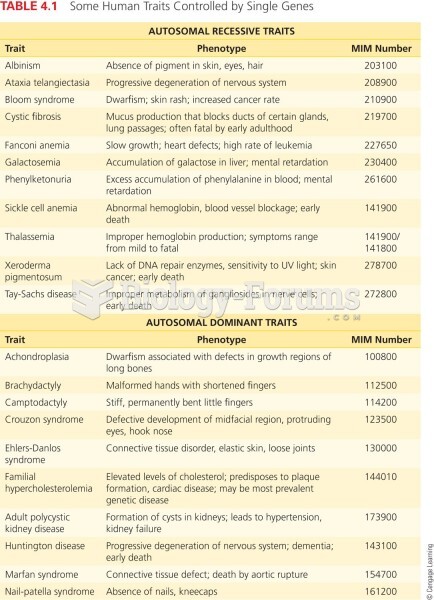
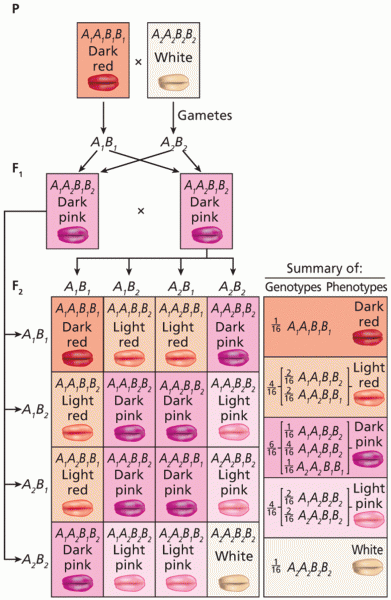
|
|
|
The first successful kidney transplant was performed in 1954 and occurred in Boston. A kidney from an identical twin was transplanted into his dying brother's body and was not rejected because it did not appear foreign to his body.
A headache when you wake up in the morning is indicative of sinusitis. Other symptoms of sinusitis can include fever, weakness, tiredness, a cough that may be more severe at night, and a runny nose or nasal congestion.
Excessive alcohol use costs the country approximately $235 billion every year.
According to the Migraine Research Foundation, migraines are the third most prevalent illness in the world. Women are most affected (18%), followed by children of both sexes (10%), and men (6%).
When taking monoamine oxidase inhibitors, people should avoid a variety of foods, which include alcoholic beverages, bean curd, broad (fava) bean pods, cheese, fish, ginseng, protein extracts, meat, sauerkraut, shrimp paste, soups, and yeast.