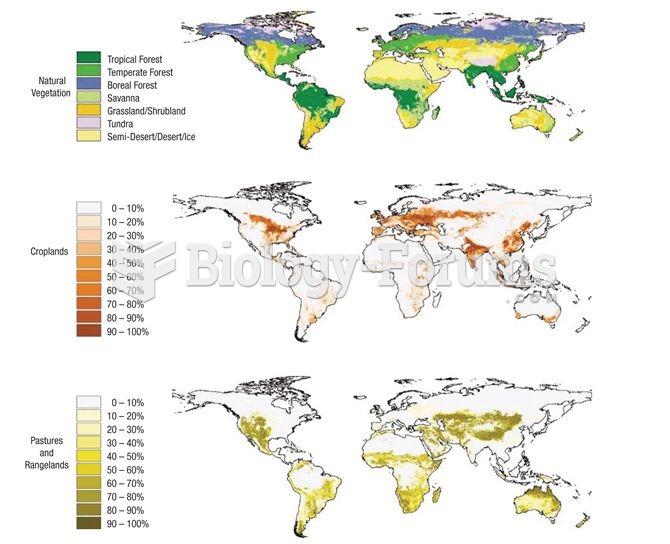
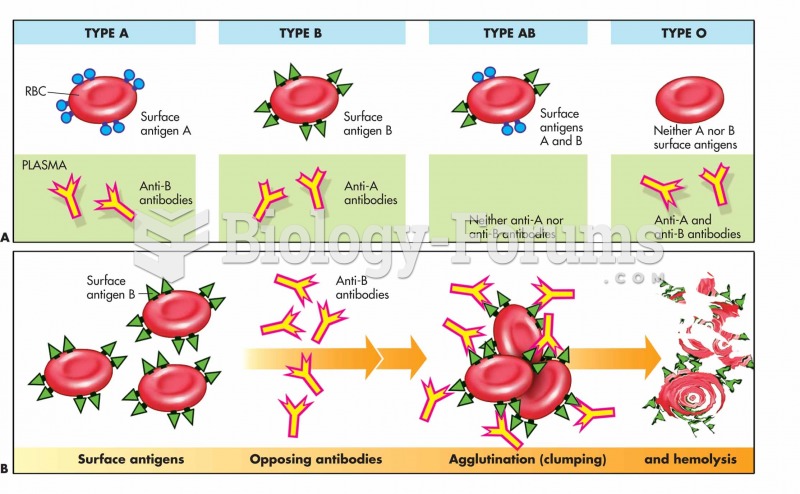
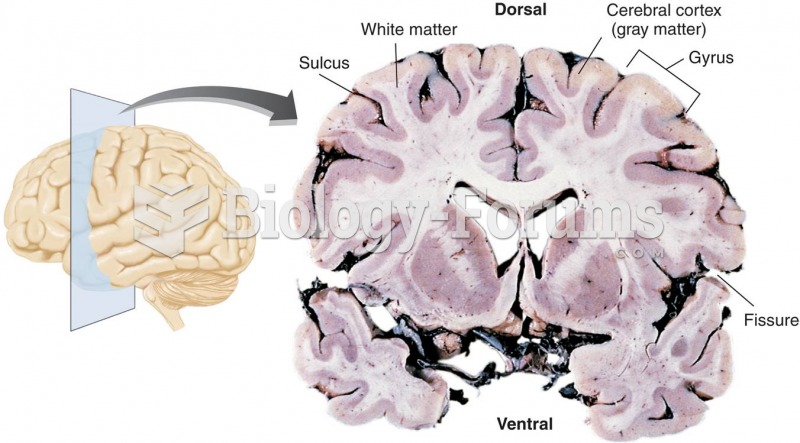
|
|
|
Did you know?
Cyanide works by making the human body unable to use oxygen.
Did you know?
It is difficult to obtain enough calcium without consuming milk or other dairy foods.
Did you know?
Asthma attacks and symptoms usually get started by specific triggers (such as viruses, allergies, gases, and air particles). You should talk to your doctor about these triggers and find ways to avoid or get rid of them.
Did you know?
The U.S. Preventive Services Task Force recommends that all women age 65 years of age or older should be screened with bone densitometry.
Did you know?
There are more sensory neurons in the tongue than in any other part of the body.