|
|
|
Street names for barbiturates include reds, red devils, yellow jackets, blue heavens, Christmas trees, and rainbows. They are commonly referred to as downers.
There are more bacteria in your mouth than there are people in the world.
In 2010, opiate painkllers, such as morphine, OxyContin®, and Vicodin®, were tied to almost 60% of drug overdose deaths.
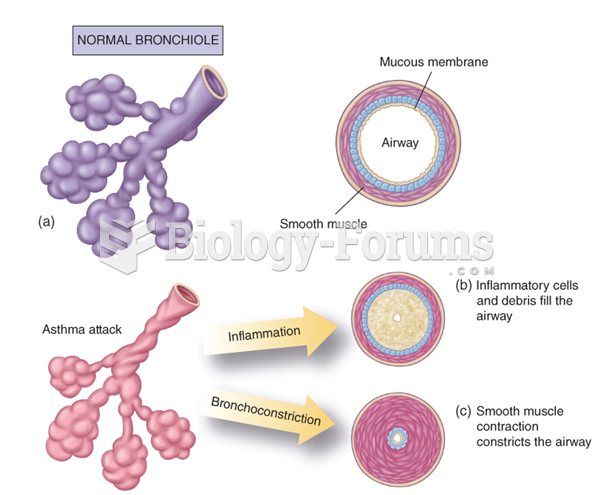
Acute bronchitis is an inflammation of the breathing tubes (bronchi), which causes increased mucus production and other changes. It is usually caused by bacteria or viruses, can be serious in people who have pulmonary or cardiac diseases, and can lead to pneumonia.
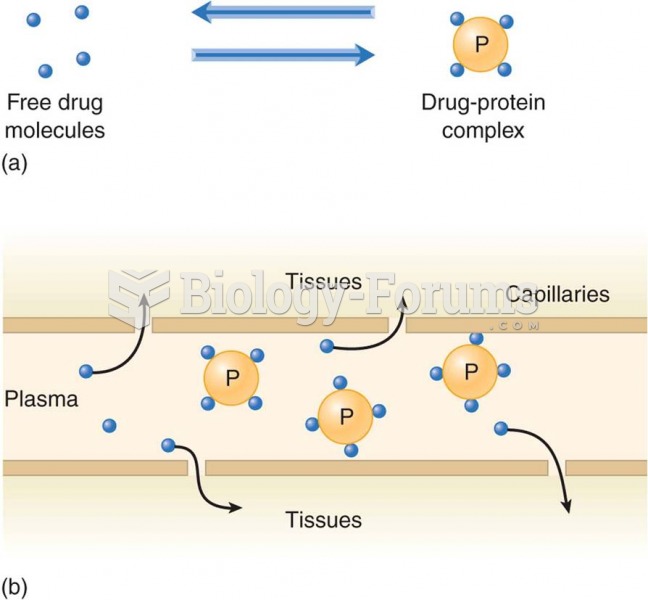
In women, pharmacodynamic differences include increased sensitivity to (and increased effectiveness of) beta-blockers, opioids, selective serotonin reuptake inhibitors, and typical antipsychotics.