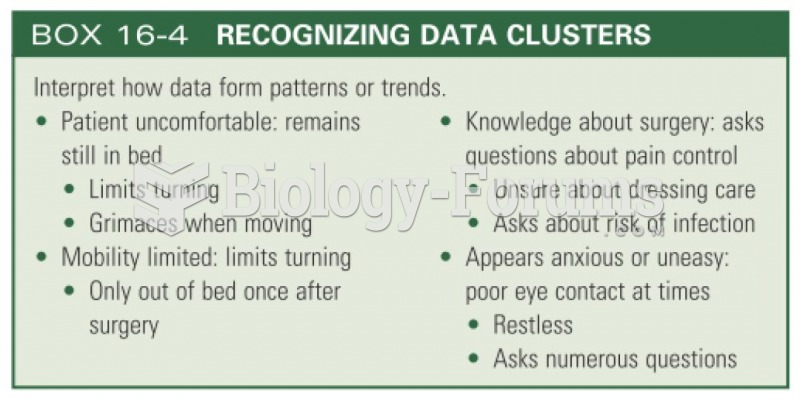
|
|
|
Signs and symptoms that may signify an eye tumor include general blurred vision, bulging eye(s), double vision, a sensation of a foreign body in the eye(s), iris defects, limited ability to move the eyelid(s), limited ability to move the eye(s), pain or discomfort in or around the eyes or eyelids, red or pink eyes, white or cloud spots on the eye(s), colored spots on the eyelid(s), swelling around the eyes, swollen eyelid(s), and general vision loss.
Only one in 10 cancer deaths is caused by the primary tumor. The vast majority of cancer mortality is caused by cells breaking away from the main tumor and metastasizing to other parts of the body, such as the brain, bones, or liver.
This year, an estimated 1.4 million Americans will have a new or recurrent heart attack.
Approximately 15–25% of recognized pregnancies end in miscarriage. However, many miscarriages often occur before a woman even knows she is pregnant.
The people with the highest levels of LDL are Mexican American males and non-Hispanic black females.