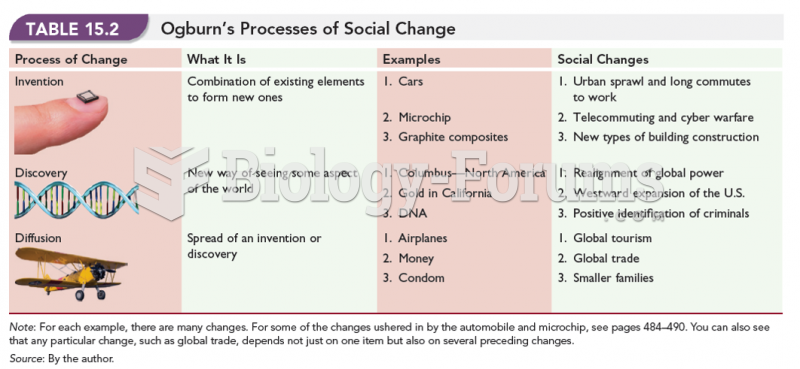
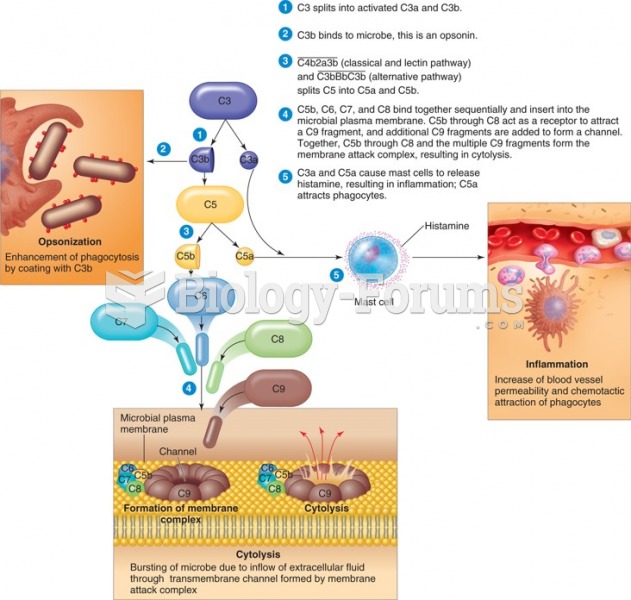
|
|
|
Fungal nail infections account for up to 30% of all skin infections. They affect 5% of the general population—mostly people over the age of 70.
Aspirin is the most widely used drug in the world. It has even been recognized as such by the Guinness Book of World Records.
Drying your hands with a paper towel will reduce the bacterial count on your hands by 45–60%.
As the western states of America were settled, pioneers often had to drink rancid water from ponds and other sources. This often resulted in chronic diarrhea, causing many cases of dehydration and death that could have been avoided if clean water had been available.
More than nineteen million Americans carry the factor V gene that causes blood clots, pulmonary embolism, and heart disease.
 This moose exploits the twigs and buds of woody plants for the food it needs to survive a cold north
This moose exploits the twigs and buds of woody plants for the food it needs to survive a cold north
 Enhanced photomicrograph showing a macrophage (purple) attack- ing bacillus Escherichia coli (green)
Enhanced photomicrograph showing a macrophage (purple) attack- ing bacillus Escherichia coli (green)