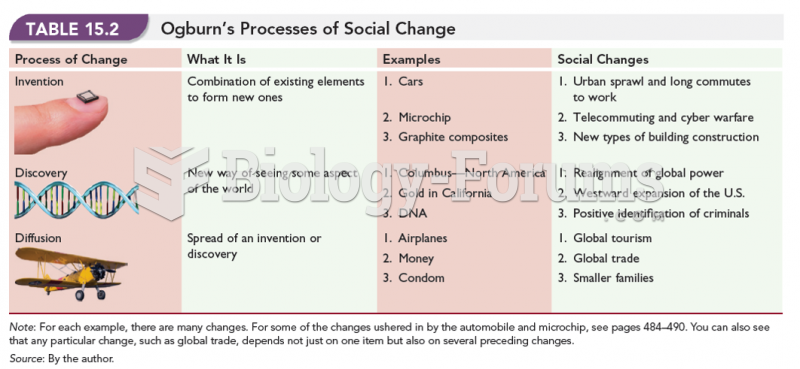
This topic contains a solution. Click here to go to the answer
|
|
|
Did you know?
Blood is approximately twice as thick as water because of the cells and other components found in it.
Did you know?
It is difficult to obtain enough calcium without consuming milk or other dairy foods.
Did you know?
Cytomegalovirus affects nearly the same amount of newborns every year as Down syndrome.
Did you know?
The liver is the only organ that has the ability to regenerate itself after certain types of damage. As much as 25% of the liver can be removed, and it will still regenerate back to its original shape and size. However, the liver cannot regenerate after severe damage caused by alcohol.
Did you know?
Most fungi that pathogenically affect humans live in soil. If a person is not healthy, has an open wound, or is immunocompromised, a fungal infection can be very aggressive.
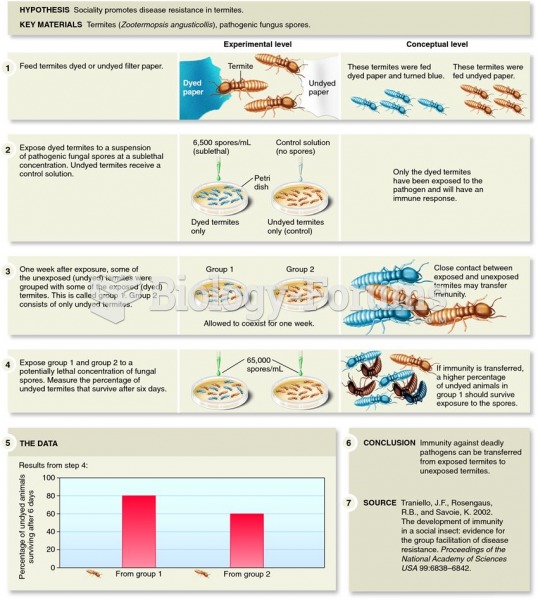 Traniello and his colleagues demonstrated that social insects may develop “social imm
Traniello and his colleagues demonstrated that social insects may develop “social imm
 Three Tasmanian devils feeding. Eating is a social event for the Tasmanian devil, and groups of 2 to
Three Tasmanian devils feeding. Eating is a social event for the Tasmanian devil, and groups of 2 to