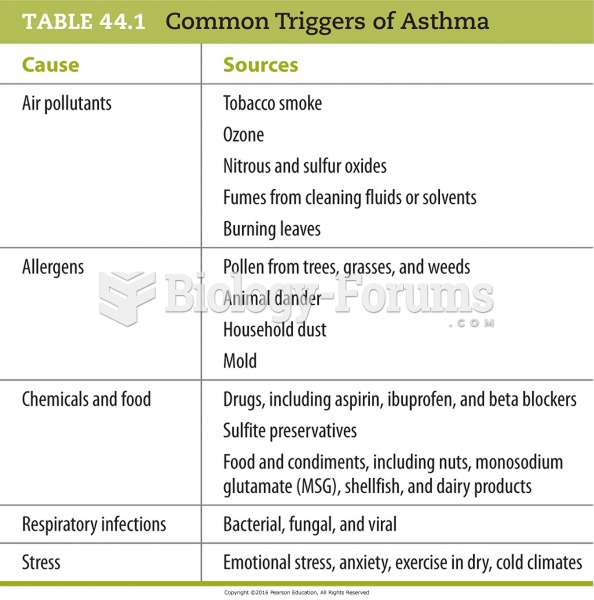
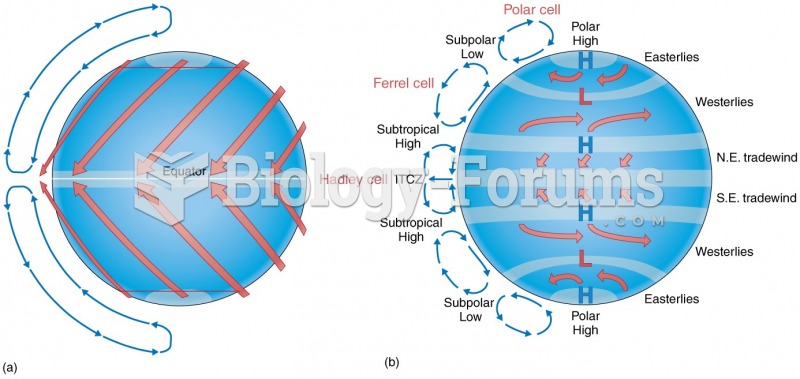
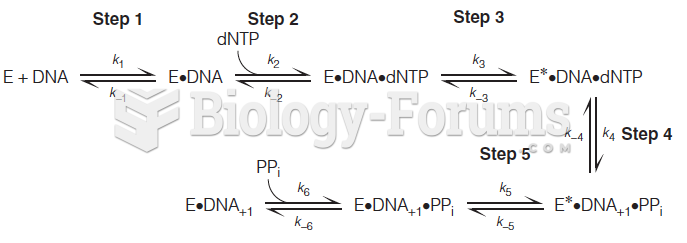
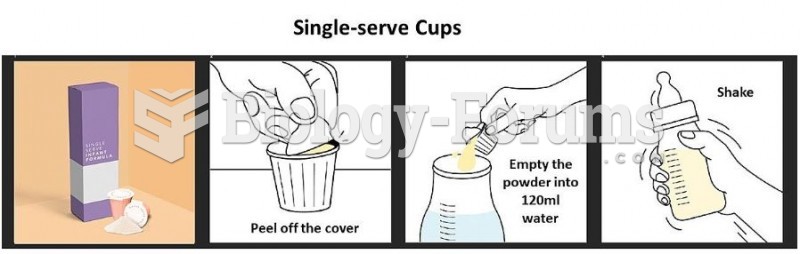
|
|
|
Your heart beats over 36 million times a year.
In the United States, congenital cytomegalovirus causes one child to become disabled almost every hour. CMV is the leading preventable viral cause of development disability in newborns. These disabilities include hearing or vision loss, and cerebral palsy.
Excessive alcohol use costs the country approximately $235 billion every year.
People about to have surgery must tell their health care providers about all supplements they take.
Bisphosphonates were first developed in the nineteenth century. They were first investigated for use in disorders of bone metabolism in the 1960s. They are now used clinically for the treatment of osteoporosis, Paget's disease, bone metastasis, multiple myeloma, and other conditions that feature bone fragility.