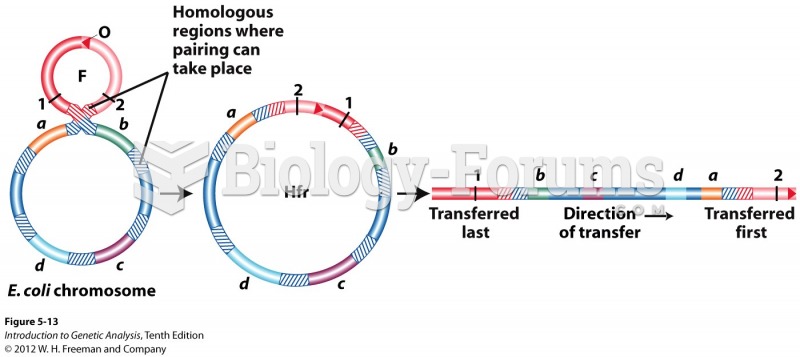
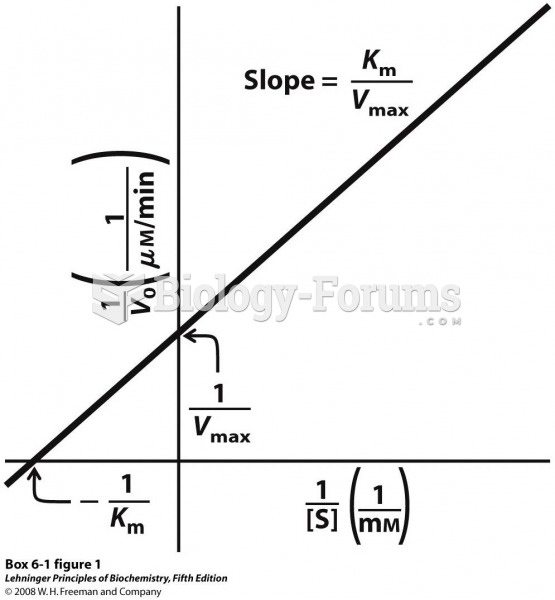
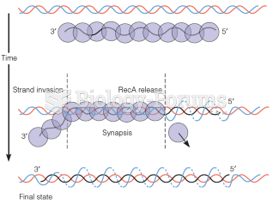
|
|
|
It is widely believed that giving a daily oral dose of aspirin to heart attack patients improves their chances of survival because the aspirin blocks the formation of new blood clots.
Colchicine is a highly poisonous alkaloid originally extracted from a type of saffron plant that is used mainly to treat gout.
If all the neurons in the human body were lined up, they would stretch more than 600 miles.
People with alcoholism are at a much greater risk of malnutrition than are other people and usually exhibit low levels of most vitamins (especially folic acid). This is because alcohol often takes the place of 50% of their daily intake of calories, with little nutritional value contained in it.
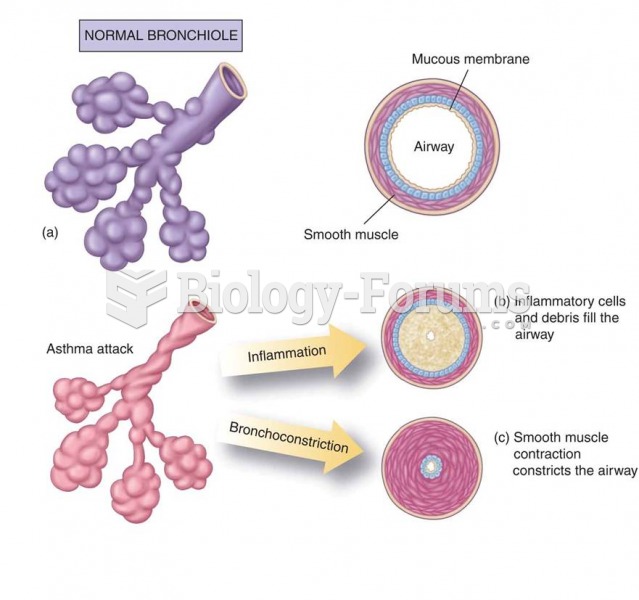
Asthma occurs in one in 11 children and in one in 12 adults. African Americans and Latinos have a higher risk for developing asthma than other groups.