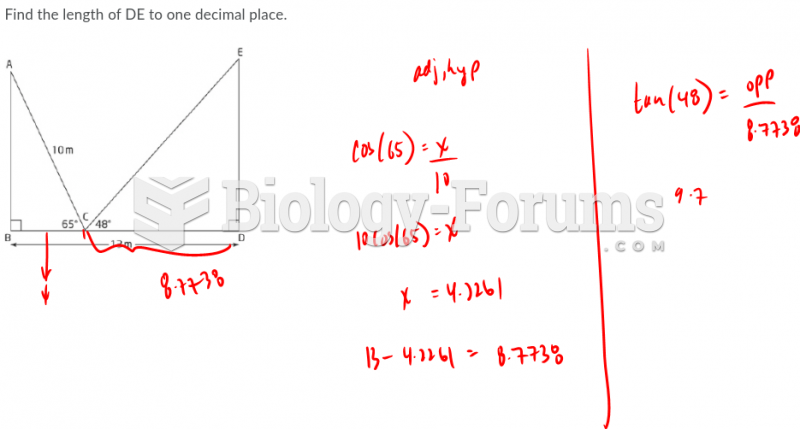
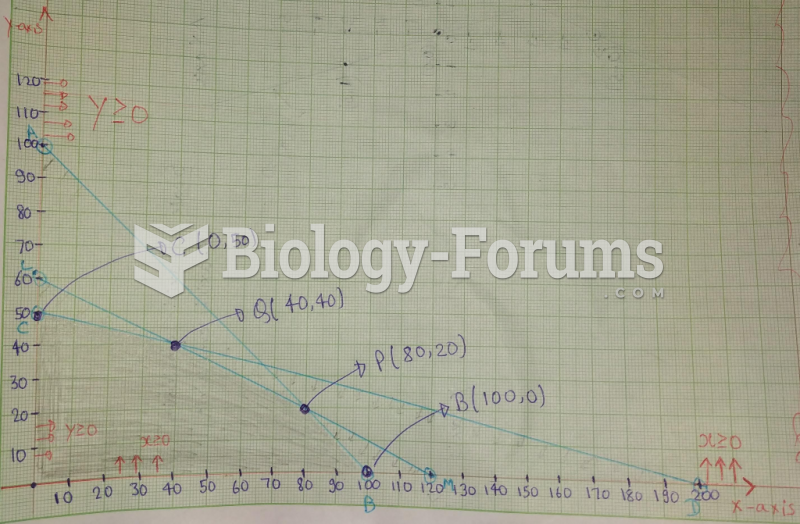
|
|
|
Studies show that systolic blood pressure can be significantly lowered by taking statins. In fact, the higher the patient's baseline blood pressure, the greater the effect of statins on his or her blood pressure.
Aspirin is the most widely used drug in the world. It has even been recognized as such by the Guinness Book of World Records.
Ether was used widely for surgeries but became less popular because of its flammability and its tendency to cause vomiting. In England, it was quickly replaced by chloroform, but this agent caused many deaths and lost popularity.
Human stomach acid is strong enough to dissolve small pieces of metal such as razor blades or staples.
For about 100 years, scientists thought that peptic ulcers were caused by stress, spicy food, and alcohol. Later, researchers added stomach acid to the list of causes and began treating ulcers with antacids. Now it is known that peptic ulcers are predominantly caused by Helicobacter pylori, a spiral-shaped bacterium that normally exist in the stomach.