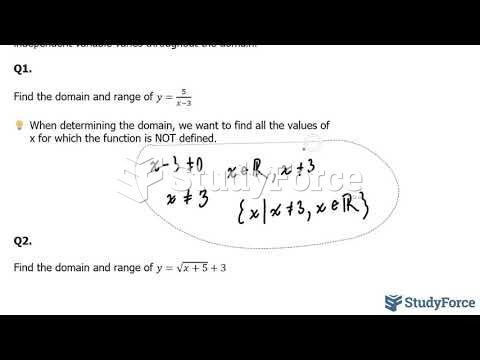
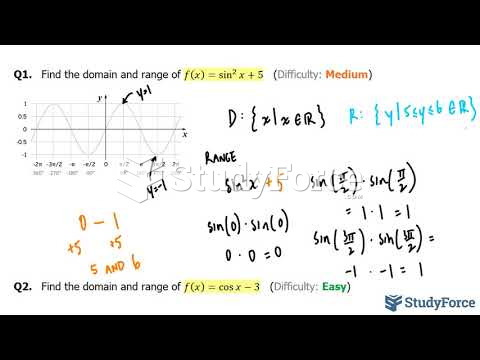
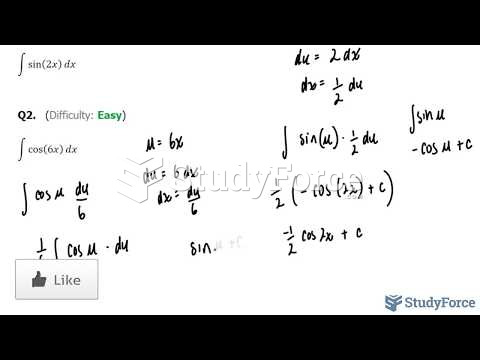
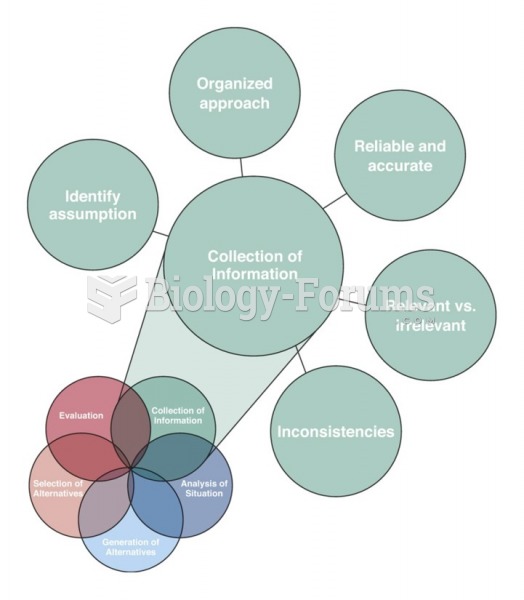
|
|
|
The most dangerous mercury compound, dimethyl mercury, is so toxic that even a few microliters spilled on the skin can cause death. Mercury has been shown to accumulate in higher amounts in the following types of fish than other types: swordfish, shark, mackerel, tilefish, crab, and tuna.
Intradermal injections are somewhat difficult to correctly administer because the skin layers are so thin that it is easy to accidentally punch through to the deeper subcutaneous layer.
Certain topical medications such as clotrimazole and betamethasone are not approved for use in children younger than 12 years of age. They must be used very cautiously, as directed by a doctor, to treat any child. Children have a much greater response to topical steroid medications.
A headache when you wake up in the morning is indicative of sinusitis. Other symptoms of sinusitis can include fever, weakness, tiredness, a cough that may be more severe at night, and a runny nose or nasal congestion.
It is difficult to obtain enough calcium without consuming milk or other dairy foods.