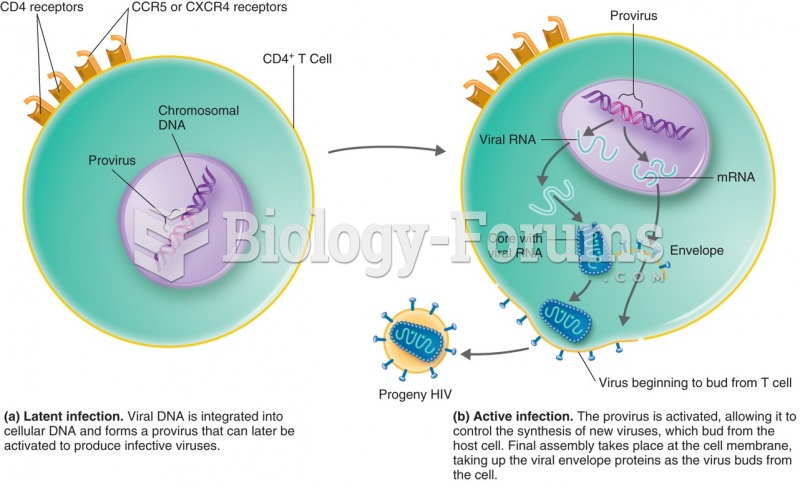
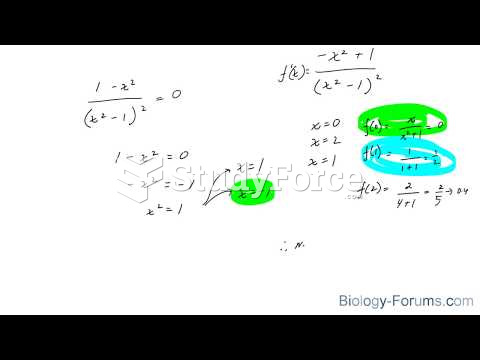
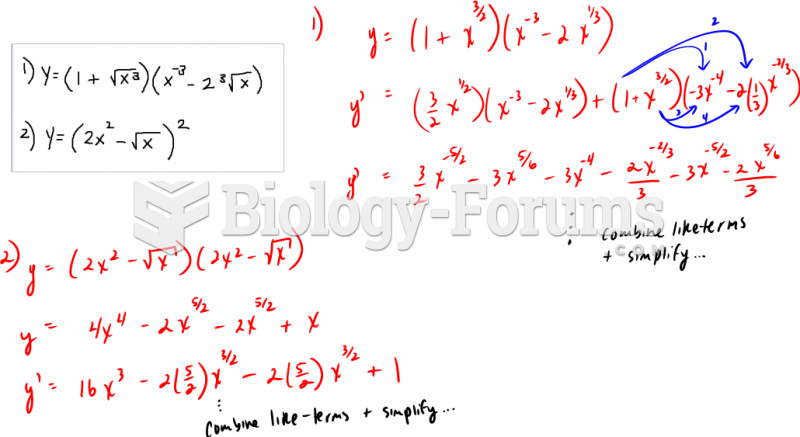
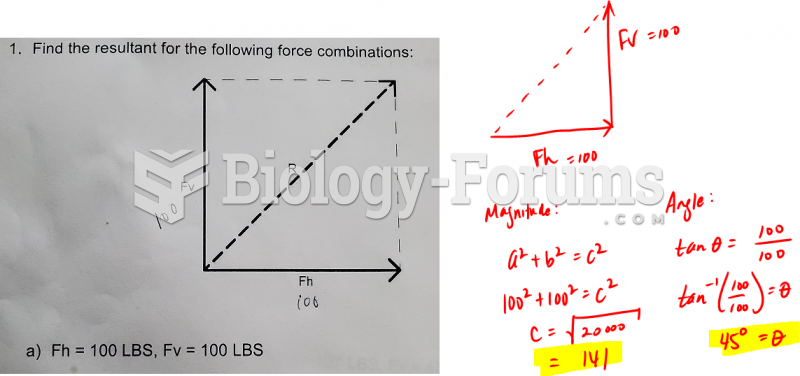
|
|
|
The people with the highest levels of LDL are Mexican American males and non-Hispanic black females.
People with alcoholism are at a much greater risk of malnutrition than are other people and usually exhibit low levels of most vitamins (especially folic acid). This is because alcohol often takes the place of 50% of their daily intake of calories, with little nutritional value contained in it.
Studies show that systolic blood pressure can be significantly lowered by taking statins. In fact, the higher the patient's baseline blood pressure, the greater the effect of statins on his or her blood pressure.
People often find it difficult to accept the idea that bacteria can be beneficial and improve health. Lactic acid bacteria are good, and when eaten, these bacteria improve health and increase longevity. These bacteria included in foods such as yogurt.
Green tea is able to stop the scent of garlic or onion from causing bad breath.