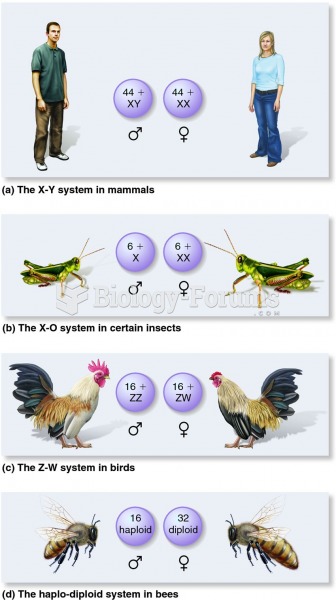
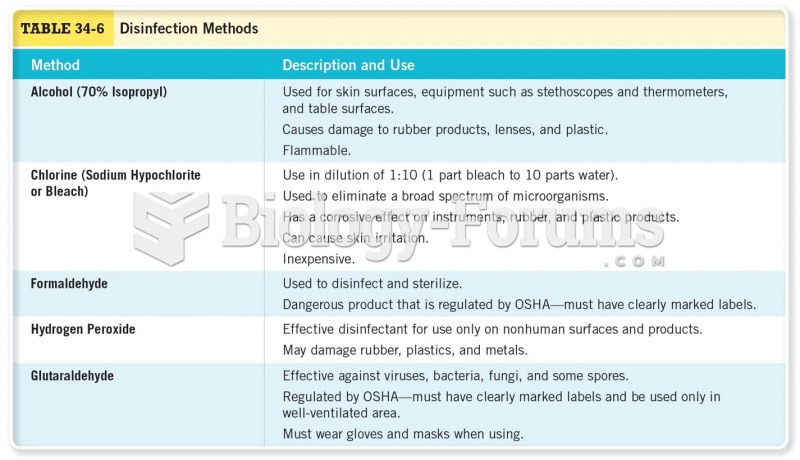
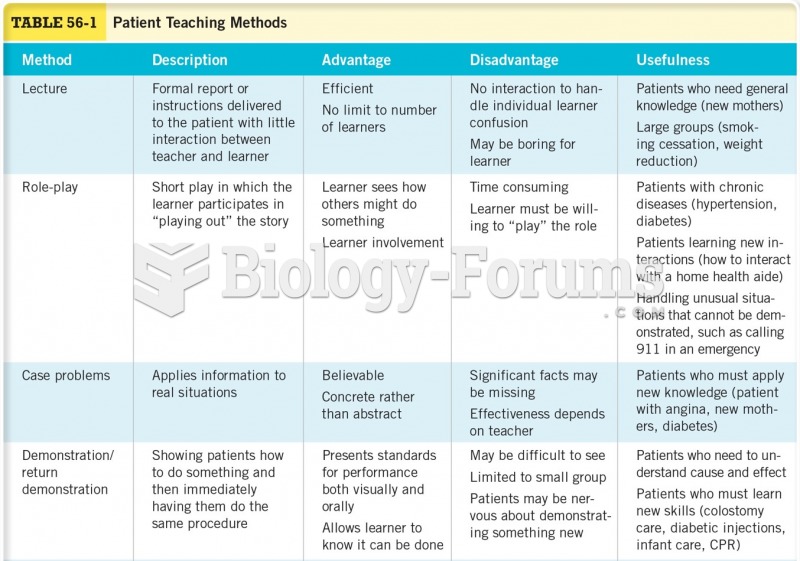
|
|
|
About one in five American adults and teenagers have had a genital herpes infection—and most of them don't know it. People with genital herpes have at least twice the risk of becoming infected with HIV if exposed to it than those people who do not have genital herpes.
The most common treatment options for addiction include psychotherapy, support groups, and individual counseling.
There used to be a metric calendar, as well as metric clocks. The metric calendar, or "French Republican Calendar" divided the year into 12 months, but each month was divided into three 10-day weeks. Each day had 10 decimal hours. Each hour had 100 decimal minutes. Due to lack of popularity, the metric clocks and calendars were ended in 1795, three years after they had been first marketed.
Barbituric acid, the base material of barbiturates, was first synthesized in 1863 by Adolph von Bayer. His company later went on to synthesize aspirin for the first time, and Bayer aspirin is still a popular brand today.
It is believed that the Incas used anesthesia. Evidence supports the theory that shamans chewed cocoa leaves and drilled holes into the heads of patients (letting evil spirits escape), spitting into the wounds they made. The mixture of cocaine, saliva, and resin numbed the site enough to allow hours of drilling.