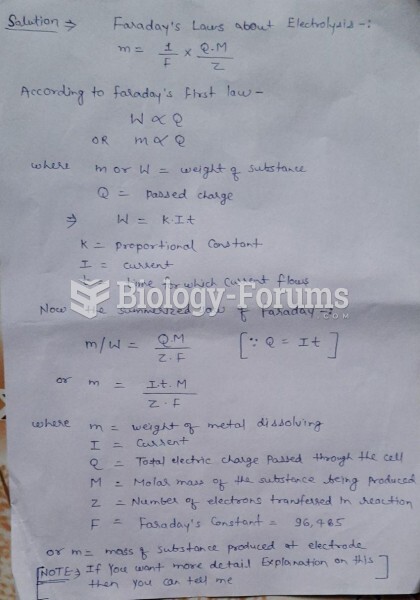
|
|
|
Pope Sylvester II tried to introduce Arabic numbers into Europe between the years 999 and 1003, but their use did not catch on for a few more centuries, and Roman numerals continued to be the primary number system.
All adults should have their cholesterol levels checked once every 5 years. During 2009–2010, 69.4% of Americans age 20 and older reported having their cholesterol checked within the last five years.
The calories found in one piece of cherry cheesecake could light a 60-watt light bulb for 1.5 hours.
Drugs are in development that may cure asthma and hay fever once and for all. They target leukotrienes, which are known to cause tightening of the air passages in the lungs and increase mucus productions in nasal passages.
The first-known contraceptive was crocodile dung, used in Egypt in 2000 BC. Condoms were also reportedly used, made of animal bladders or intestines.
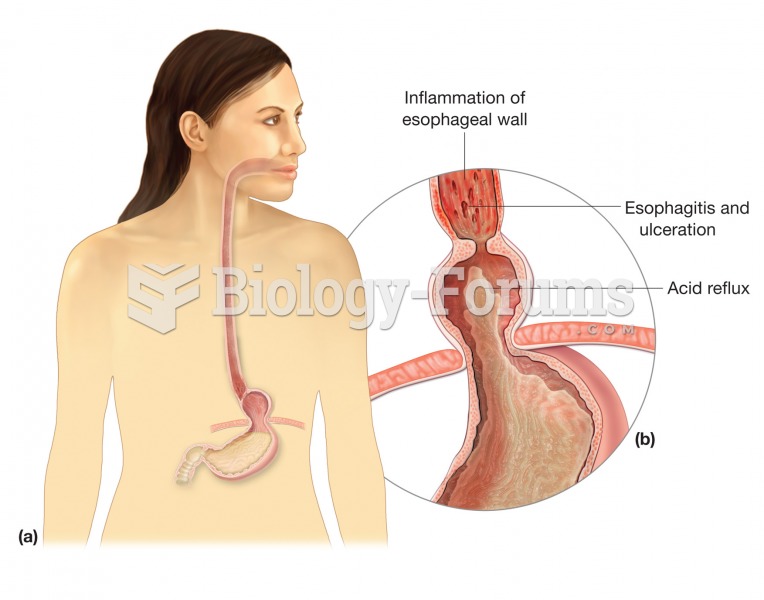 Hiatal hernia. (a) The hernia occurs when the stomach protrudes through the diaphragm and into the t
Hiatal hernia. (a) The hernia occurs when the stomach protrudes through the diaphragm and into the t
 A passenger train crosses Stony Creek Bridge in the Rocky Mountains in 1878. Railroads were importan
A passenger train crosses Stony Creek Bridge in the Rocky Mountains in 1878. Railroads were importan
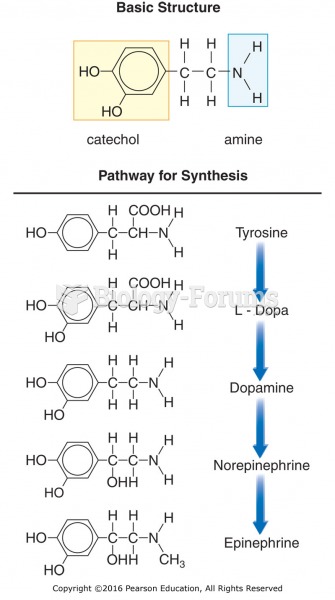 Basic chemical structure and synthesis of catecholamines. The synthesis of norepinephrine occurs in ...
Basic chemical structure and synthesis of catecholamines. The synthesis of norepinephrine occurs in ...