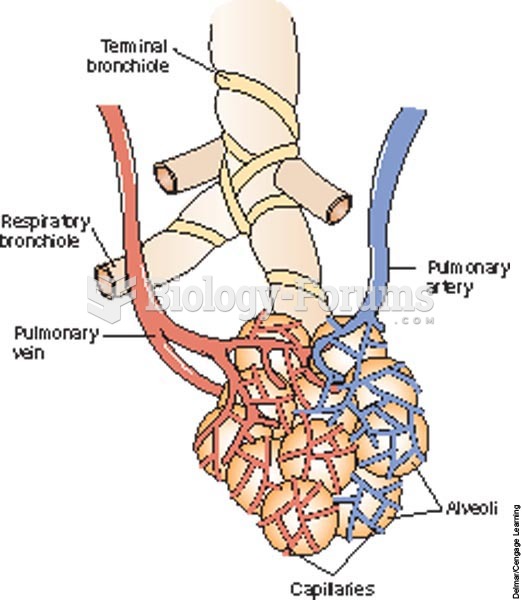
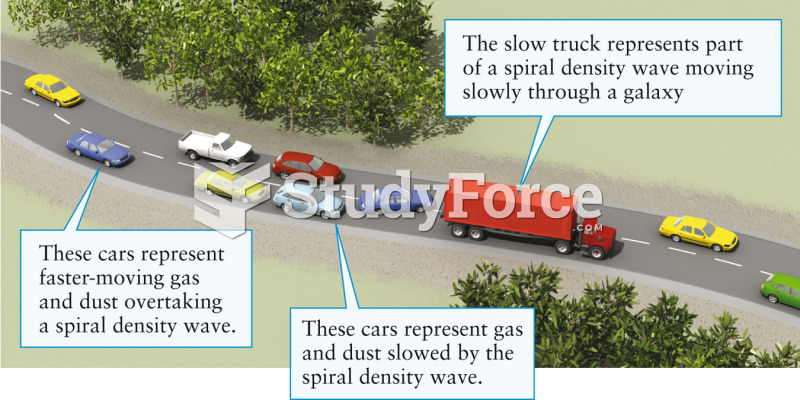
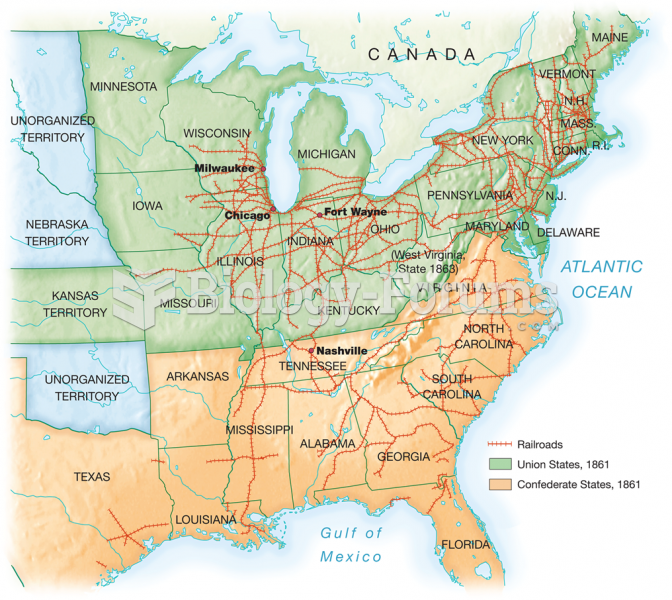
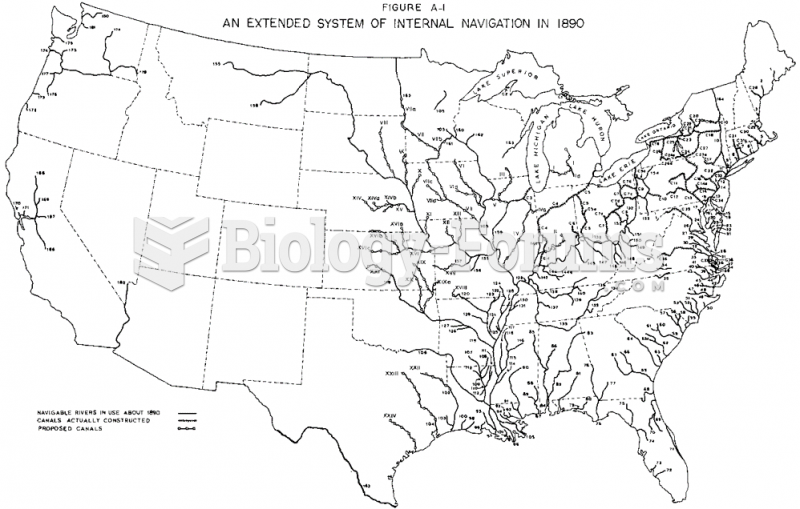
|
|
|
The first-known contraceptive was crocodile dung, used in Egypt in 2000 BC. Condoms were also reportedly used, made of animal bladders or intestines.
Over time, chronic hepatitis B virus and hepatitis C virus infections can progress to advanced liver disease, liver failure, and hepatocellular carcinoma. Unlike other forms, more than 80% of hepatitis C infections become chronic and lead to liver disease. When combined with hepatitis B, hepatitis C now accounts for 75% percent of all cases of liver disease around the world. Liver failure caused by hepatitis C is now leading cause of liver transplants in the United States.
More than 4.4billion prescriptions were dispensed within the United States in 2016.
Cyanide works by making the human body unable to use oxygen.
A seasonal flu vaccine is the best way to reduce the chances you will get seasonal influenza and spread it to others.