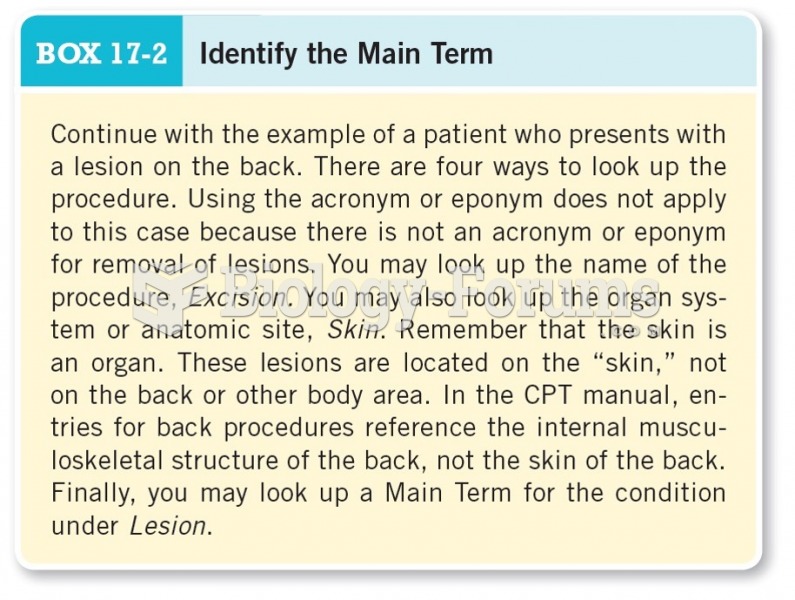
|
|
|
Only one in 10 cancer deaths is caused by the primary tumor. The vast majority of cancer mortality is caused by cells breaking away from the main tumor and metastasizing to other parts of the body, such as the brain, bones, or liver.
Every flu season is different, and even healthy people can get extremely sick from the flu, as well as spread it to others. The flu season can begin as early as October and last as late as May. Every person over six months of age should get an annual flu vaccine. The vaccine cannot cause you to get influenza, but in some seasons, may not be completely able to prevent you from acquiring influenza due to changes in causative viruses. The viruses in the flu shot are killed—there is no way they can give you the flu. Minor side effects include soreness, redness, or swelling where the shot was given. It is possible to develop a slight fever, and body aches, but these are simply signs that the body is responding to the vaccine and making itself ready to fight off the influenza virus should you come in contact with it.
The Food and Drug Administration has approved Risperdal, an adult antipsychotic drug, for the symptomatic treatment of irritability in children and adolescents with autism. The approval is the first for the use of a drug to treat behaviors associated with autism in children. These behaviors are included under the general heading of irritability and include aggression, deliberate self-injury, and temper tantrums.
Liver spots have nothing whatsoever to do with the liver. They are a type of freckles commonly seen in older adults who have been out in the sun without sufficient sunscreen.
All patients with hyperparathyroidism will develop osteoporosis. The parathyroid glands maintain blood calcium within the normal range. All patients with this disease will continue to lose calcium from their bones every day, and there is no way to prevent the development of osteoporosis as a result.