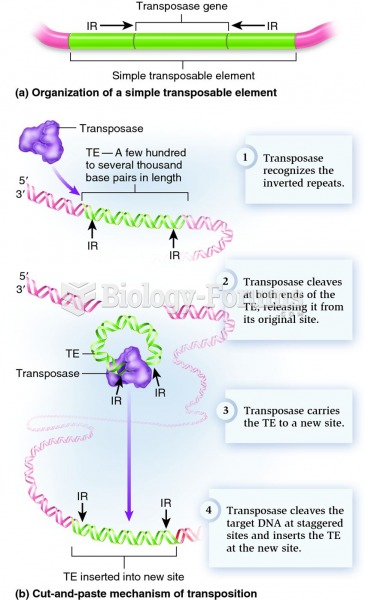
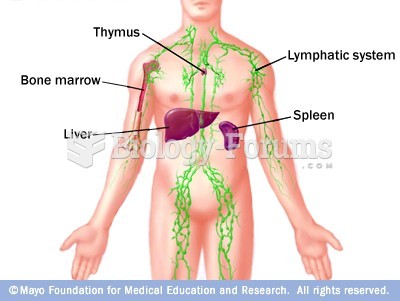
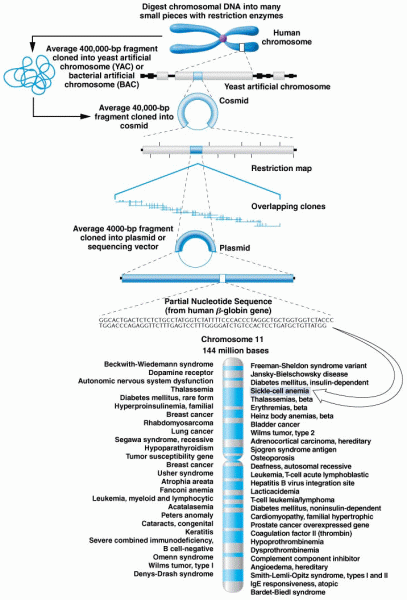
|
|
|
Adolescents often feel clumsy during puberty because during this time of development, their hands and feet grow faster than their arms and legs do. The body is therefore out of proportion. One out of five adolescents actually experiences growing pains during this period.
Complications of influenza include: bacterial pneumonia, ear and sinus infections, dehydration, and worsening of chronic conditions such as asthma, congestive heart failure, or diabetes.
An identified risk factor for osteoporosis is the intake of excessive amounts of vitamin A. Dietary intake of approximately double the recommended daily amount of vitamin A, by women, has been shown to reduce bone mineral density and increase the chances for hip fractures compared with women who consumed the recommended daily amount (or less) of vitamin A.
People often find it difficult to accept the idea that bacteria can be beneficial and improve health. Lactic acid bacteria are good, and when eaten, these bacteria improve health and increase longevity. These bacteria included in foods such as yogurt.
As of mid-2016, 18.2 million people were receiving advanced retroviral therapy (ART) worldwide. This represents between 43–50% of the 34–39.8 million people living with HIV.