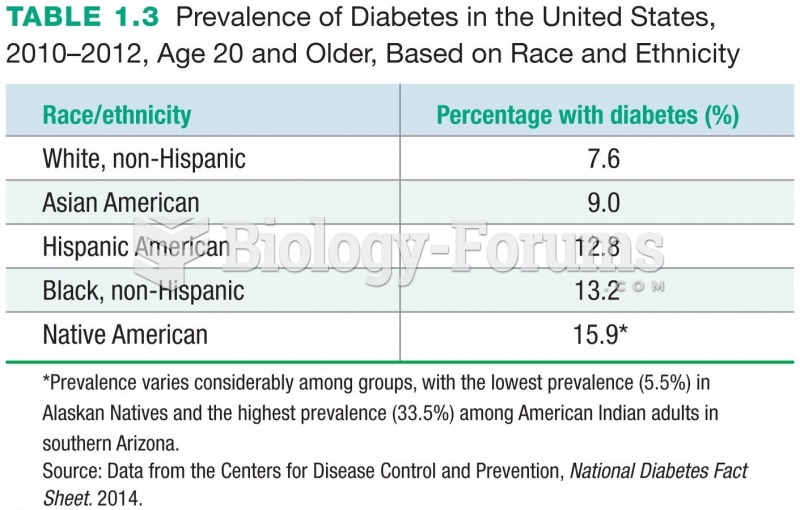
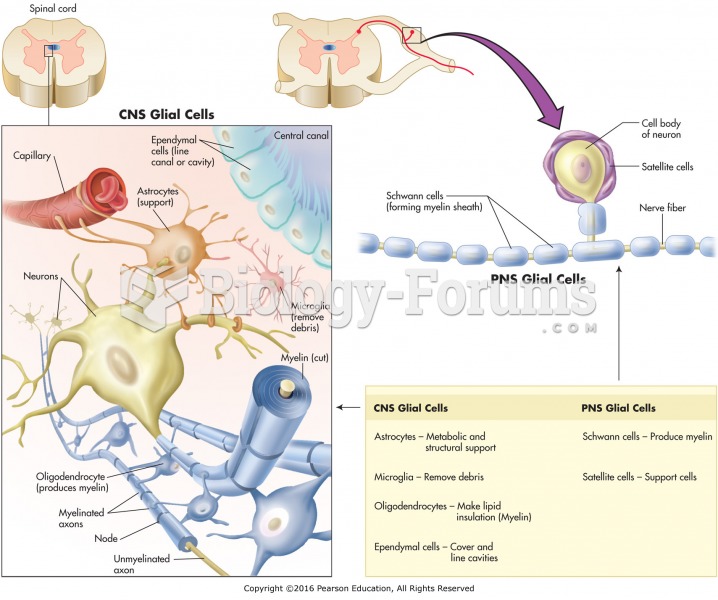
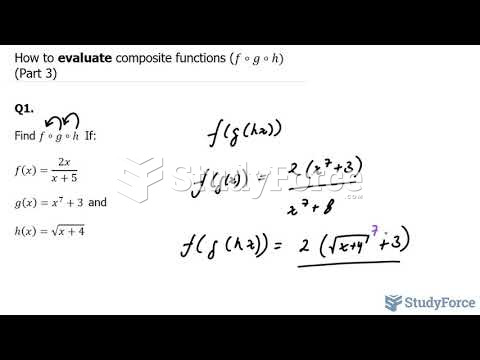
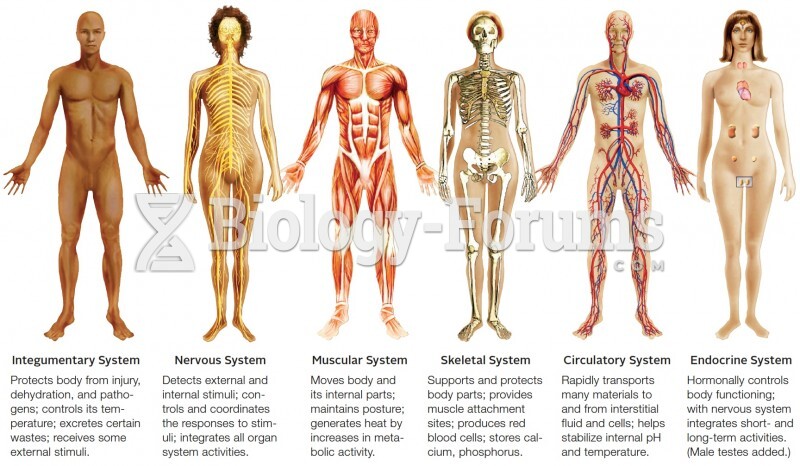
|
|
|
There can actually be a 25-hour time difference between certain locations in the world. The International Date Line passes between the islands of Samoa and American Samoa. It is not a straight line, but "zig-zags" around various island chains. Therefore, Samoa and nearby islands have one date, while American Samoa and nearby islands are one day behind. Daylight saving time is used in some islands, but not in others—further shifting the hours out of sync with natural time.
When blood is deoxygenated and flowing back to the heart through the veins, it is dark reddish-blue in color. Blood in the arteries that is oxygenated and flowing out to the body is bright red. Whereas arterial blood comes out in spurts, venous blood flows.
A serious new warning has been established for pregnant women against taking ACE inhibitors during pregnancy. In the study, the risk of major birth defects in children whose mothers took ACE inhibitors during the first trimester was nearly three times higher than in children whose mothers didn't take ACE inhibitors. Physicians can prescribe alternative medications for pregnant women who have symptoms of high blood pressure.
To prove that stomach ulcers were caused by bacteria and not by stress, a researcher consumed an entire laboratory beaker full of bacterial culture. After this, he did indeed develop stomach ulcers, and won the Nobel Prize for his discovery.
Patients should never assume they are being given the appropriate drugs. They should make sure they know which drugs are being prescribed, and always double-check that the drugs received match the prescription.