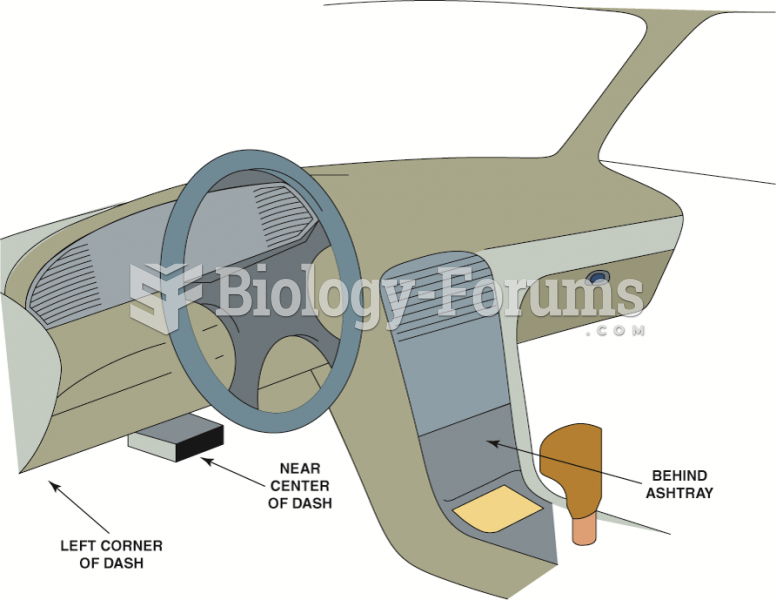
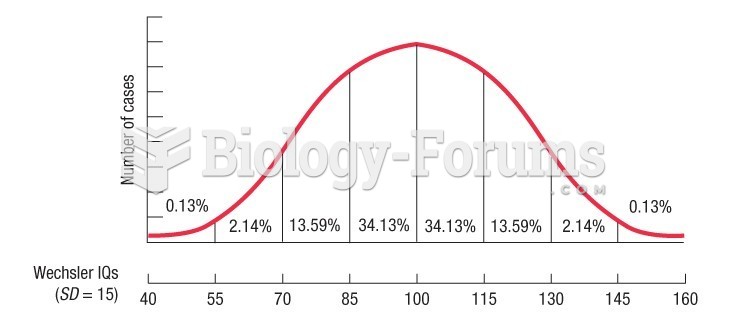
|
|
|
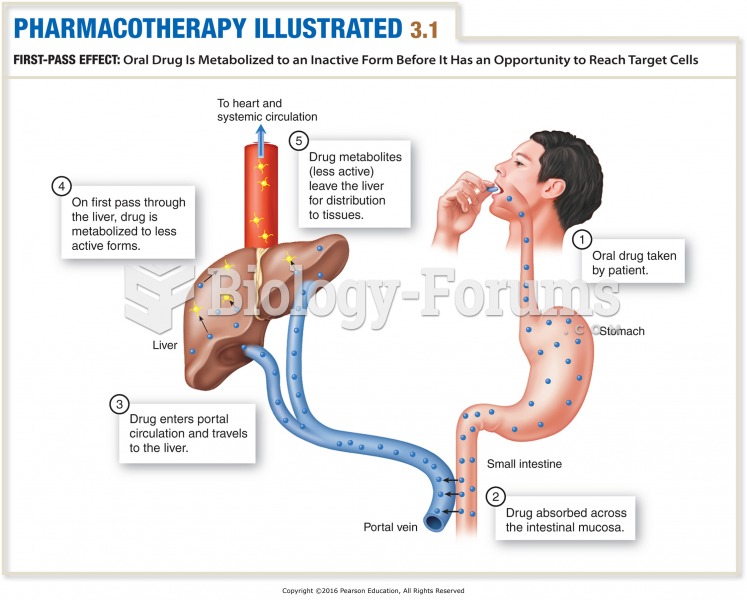
The human body's pharmacokinetics are quite varied. Our hair holds onto drugs longer than our urine, blood, or saliva. For example, alcohol can be detected in the hair for up to 90 days after it was consumed. The same is true for marijuana, cocaine, ecstasy, heroin, methamphetamine, and nicotine.
Essential fatty acids have been shown to be effective against ulcers, asthma, dental cavities, and skin disorders such as acne.
More than one-third of adult Americans are obese. Diseases that kill the largest number of people annually, such as heart disease, cancer, diabetes, stroke, and hypertension, can be attributed to diet.
As of mid-2016, 18.2 million people were receiving advanced retroviral therapy (ART) worldwide. This represents between 43–50% of the 34–39.8 million people living with HIV.
Amoebae are the simplest type of protozoans, and are characterized by a feeding and dividing trophozoite stage that moves by temporary extensions called pseudopodia or false feet.