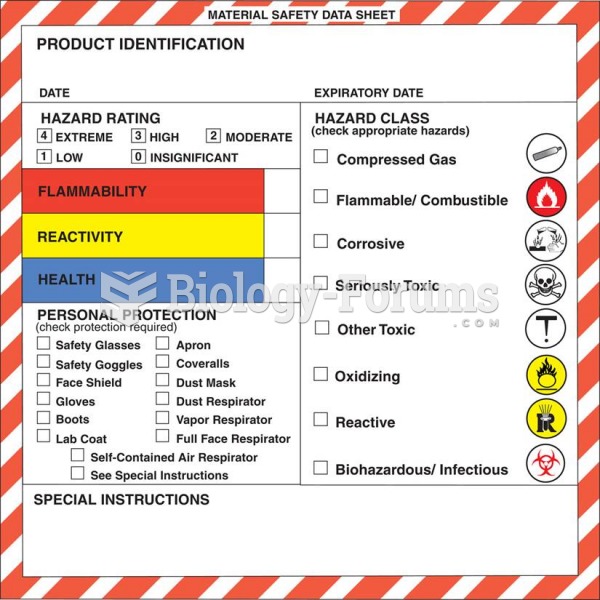
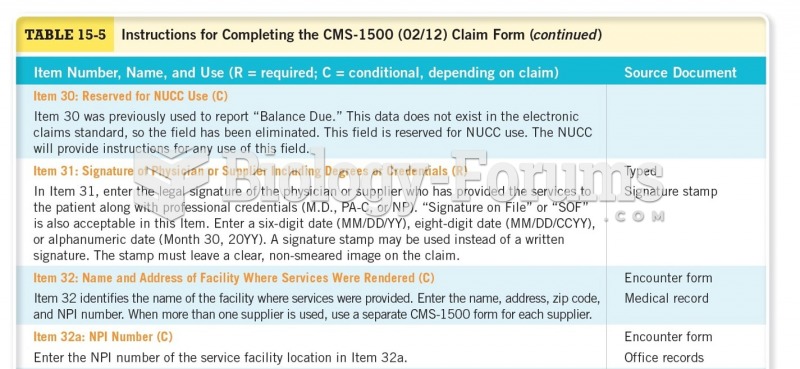
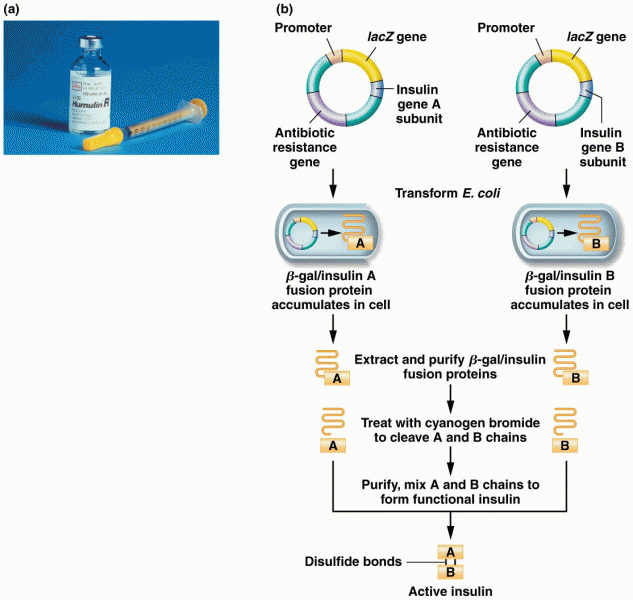
|
|
|
The training of an anesthesiologist typically requires four years of college, 4 years of medical school, 1 year of internship, and 3 years of residency.
Coca-Cola originally used coca leaves and caffeine from the African kola nut. It was advertised as a therapeutic agent and "pickerupper." Eventually, its formulation was changed, and the coca leaves were removed because of the effects of regulation on cocaine-related products.
Many of the drugs used by neuroscientists are derived from toxic plants and venomous animals (such as snakes, spiders, snails, and puffer fish).
The people with the highest levels of LDL are Mexican American males and non-Hispanic black females.
For pediatric patients, intravenous fluids are the most commonly cited products involved in medication errors that are reported to the USP.