|
|
|
This year, an estimated 1.4 million Americans will have a new or recurrent heart attack.
Nitroglycerin is used to alleviate various heart-related conditions, and it is also the chief component of dynamite (but mixed in a solid clay base to stabilize it).
A cataract is a clouding of the eyes' natural lens. As we age, some clouding of the lens may occur. The first sign of a cataract is usually blurry vision. Although glasses and other visual aids may at first help a person with cataracts, surgery may become inevitable. Cataract surgery is very successful in restoring vision, and it is the most frequently performed surgery in the United States.
Anesthesia awareness is a potentially disturbing adverse effect wherein patients who have been paralyzed with muscle relaxants may awaken. They may be aware of their surroundings but unable to communicate or move. Neurologic monitoring equipment that helps to more closely check the patient's anesthesia stages is now available to avoid the occurrence of anesthesia awareness.
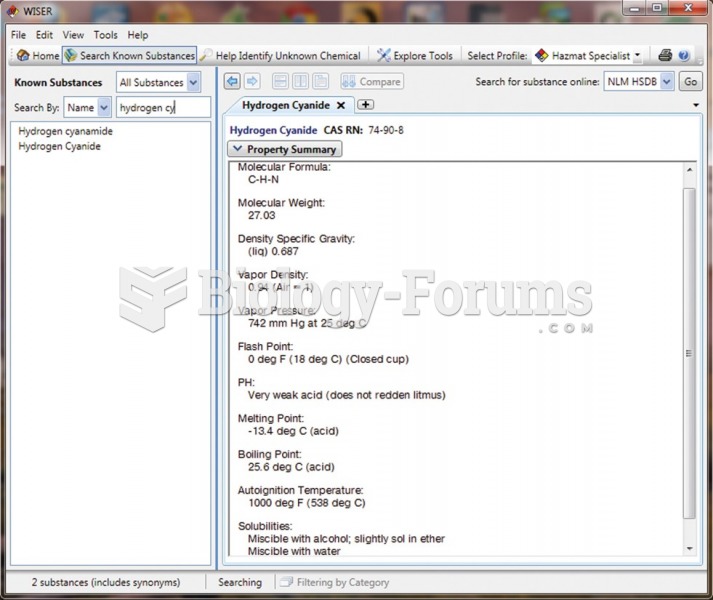
Certain rare plants containing cyanide include apricot pits and a type of potato called cassava. Fortunately, only chronic or massive ingestion of any of these plants can lead to serious poisoning.