|
|
|
According to the CDC, approximately 31.7% of the U.S. population has high low-density lipoprotein (LDL) or "bad cholesterol" levels.
The first documented use of surgical anesthesia in the United States was in Connecticut in 1844.
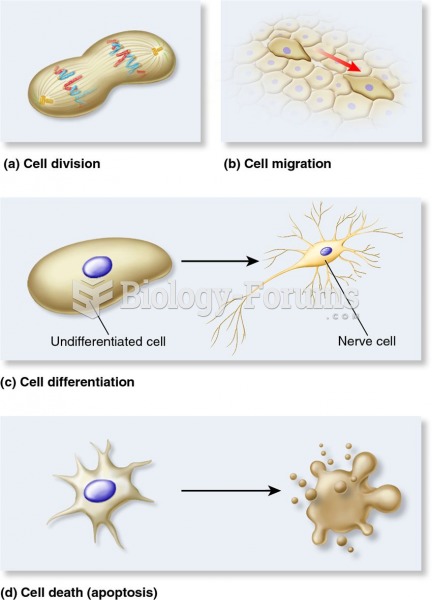
There are more nerve cells in one human brain than there are stars in the Milky Way.
Egg cells are about the size of a grain of sand. They are formed inside of a female's ovaries before she is even born.
The top 10 most important tips that will help you grow old gracefully include (1) quit smoking, (2) keep your weight down, (3) take supplements, (4) skip a meal each day or fast 1 day per week, (5) get a pet, (6) get medical help for chronic pain, (7) walk regularly, (8) reduce arguments, (9) put live plants in your living space, and (10) do some weight training.