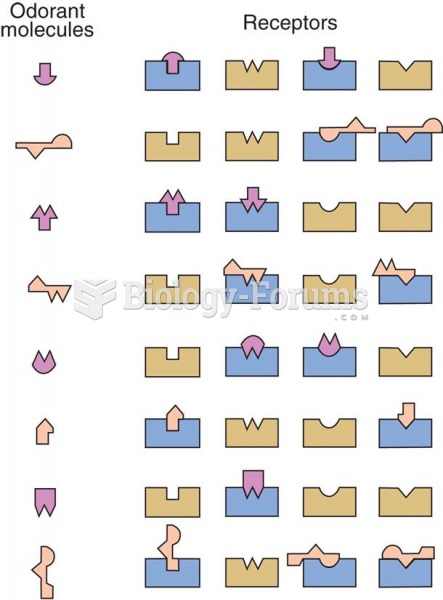
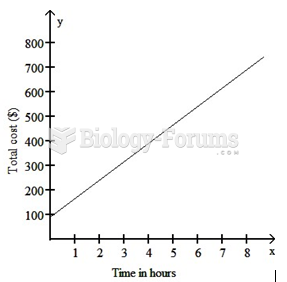
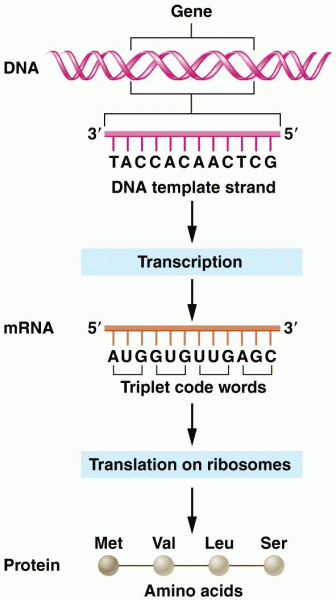
|
|
|
Hippocrates noted that blood separates into four differently colored liquids when removed from the body and examined: a pure red liquid mixed with white liquid material with a yellow-colored froth at the top and a black substance that settles underneath; he named these the four humors (for blood, phlegm, yellow bile, and black bile).
Certain rare plants containing cyanide include apricot pits and a type of potato called cassava. Fortunately, only chronic or massive ingestion of any of these plants can lead to serious poisoning.
Elderly adults are living longer, and causes of death are shifting. At the same time, autopsy rates are at or near their lowest in history.
Many people have small pouches in their colons that bulge outward through weak spots. Each pouch is called a diverticulum. About 10% of Americans older than age 40 years have diverticulosis, which, when the pouches become infected or inflamed, is called diverticulitis. The main cause of diverticular disease is a low-fiber diet.
Addicts to opiates often avoid treatment because they are afraid of withdrawal. Though unpleasant, with proper management, withdrawal is rarely fatal and passes relatively quickly.