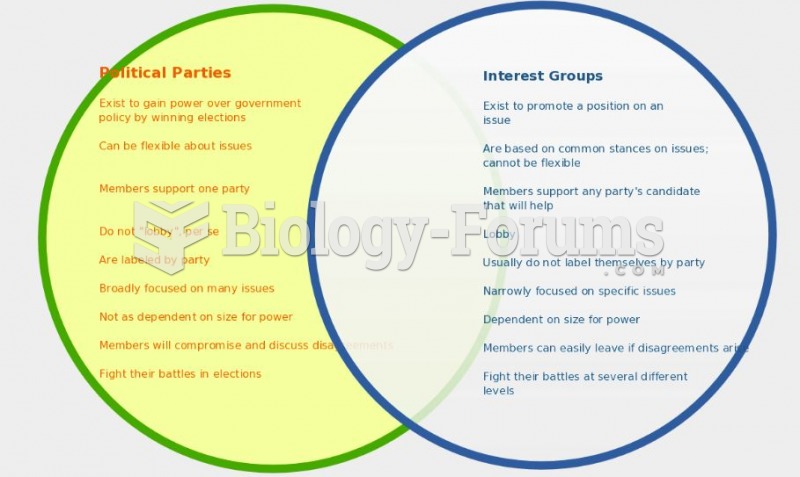
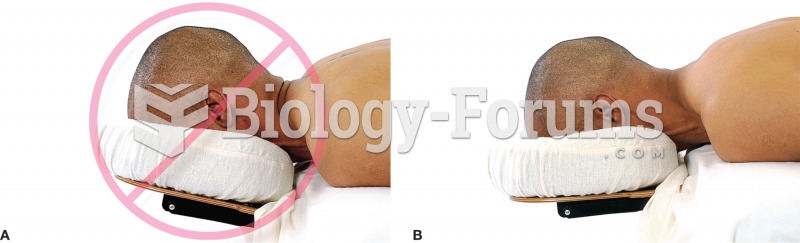
|
|
|
To prove that stomach ulcers were caused by bacteria and not by stress, a researcher consumed an entire laboratory beaker full of bacterial culture. After this, he did indeed develop stomach ulcers, and won the Nobel Prize for his discovery.
People often find it difficult to accept the idea that bacteria can be beneficial and improve health. Lactic acid bacteria are good, and when eaten, these bacteria improve health and increase longevity. These bacteria included in foods such as yogurt.
Of the estimated 2 million heroin users in the United States, 600,000–800,000 are considered hardcore addicts. Heroin addiction is considered to be one of the hardest addictions to recover from.
People about to have surgery must tell their health care providers about all supplements they take.
The Centers for Disease Control and Prevention has released reports detailing the deaths of infants (younger than 1 year of age) who died after being given cold and cough medications. This underscores the importance of educating parents that children younger than 2 years of age should never be given over-the-counter cold and cough medications without consulting their physicians.