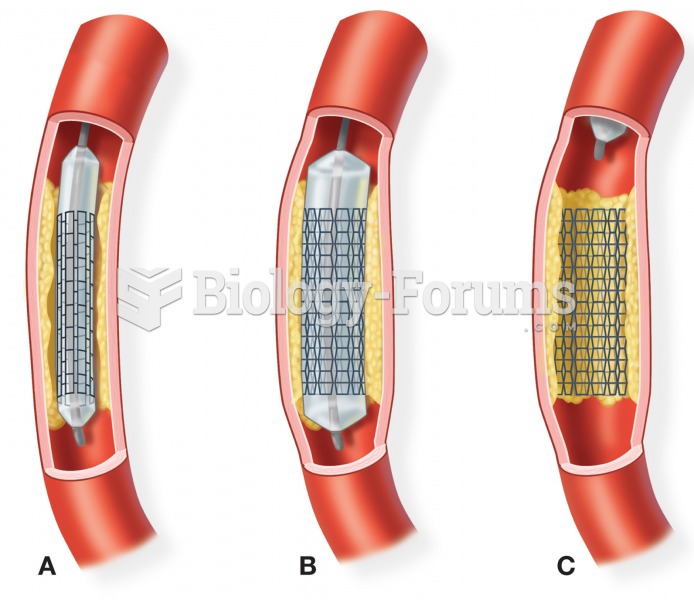
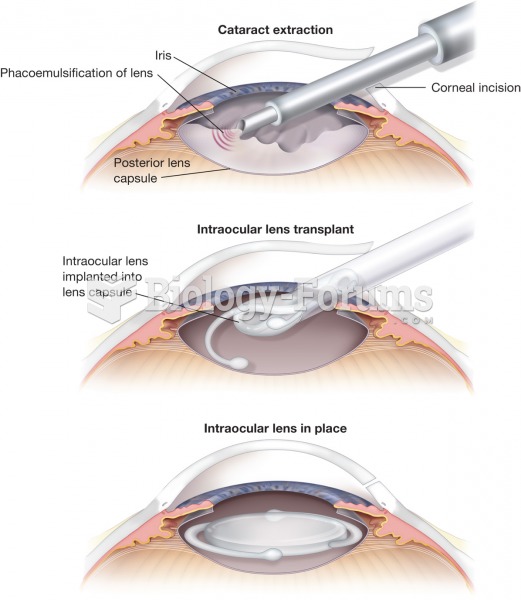
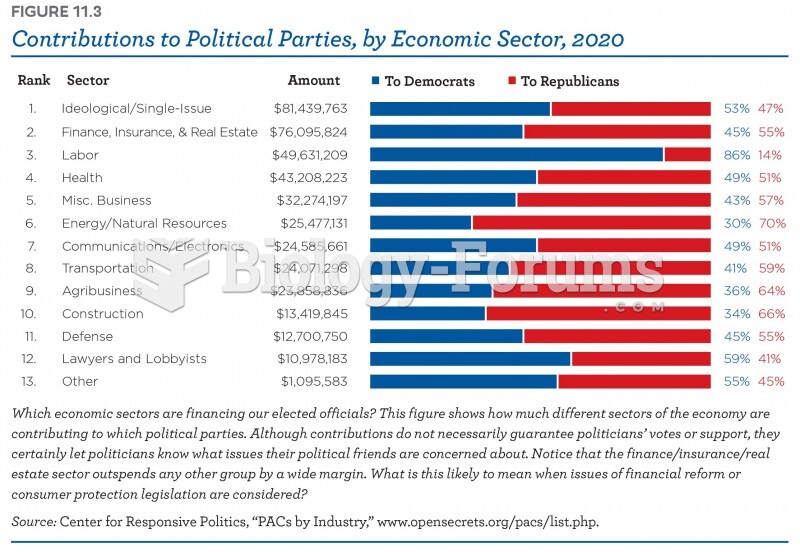
This topic contains a solution. Click here to go to the answer
|
|
|
Did you know?
Anti-aging claims should not ever be believed. There is no supplement, medication, or any other substance that has been proven to slow or stop the aging process.
Did you know?
Serum cholesterol testing in adults is recommended every 1 to 5 years. People with diabetes and a family history of high cholesterol should be tested even more frequently.
Did you know?
Thyroid conditions may make getting pregnant impossible.
Did you know?
Street names for barbiturates include reds, red devils, yellow jackets, blue heavens, Christmas trees, and rainbows. They are commonly referred to as downers.
Did you know?
In 2012, nearly 24 milliion Americans, aged 12 and older, had abused an illicit drug, according to the National Institute on Drug Abuse (NIDA).