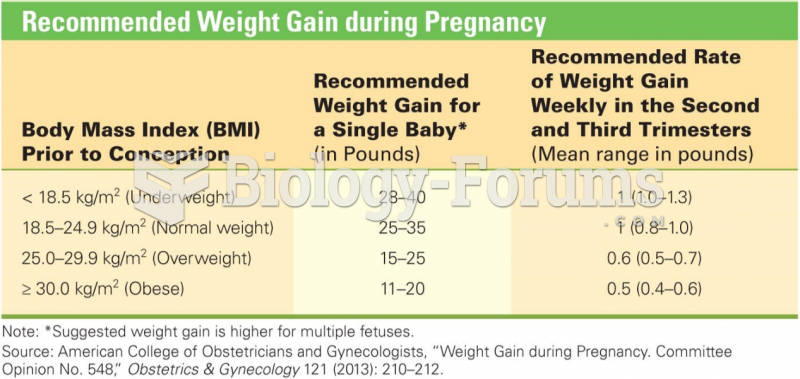
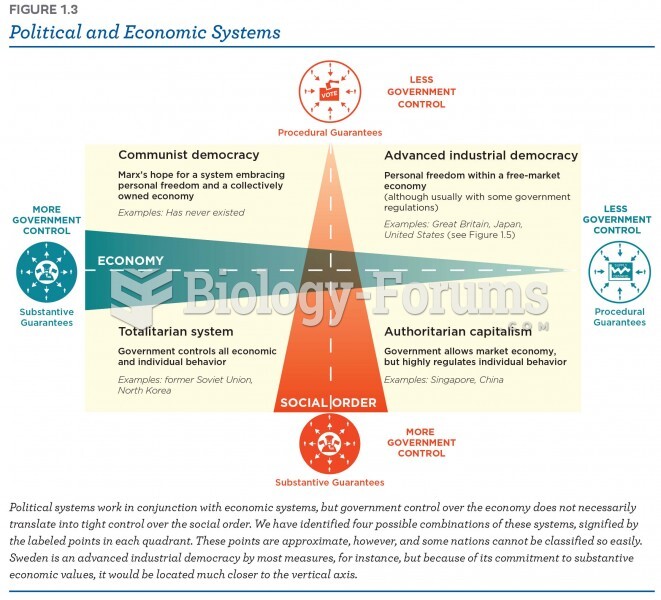
|
|
|
Bacteria have flourished on the earth for over three billion years. They were the first life forms on the planet.
A headache when you wake up in the morning is indicative of sinusitis. Other symptoms of sinusitis can include fever, weakness, tiredness, a cough that may be more severe at night, and a runny nose or nasal congestion.
Addicts to opiates often avoid treatment because they are afraid of withdrawal. Though unpleasant, with proper management, withdrawal is rarely fatal and passes relatively quickly.
Sperm cells are so tiny that 400 to 500 million (400,000,000–500,000,000) of them fit onto 1 tsp.
The cure for trichomoniasis is easy as long as the patient does not drink alcoholic beverages for 24 hours. Just a single dose of medication is needed to rid the body of the disease. However, without proper precautions, an individual may contract the disease repeatedly. In fact, most people develop trichomoniasis again within three months of their last treatment.
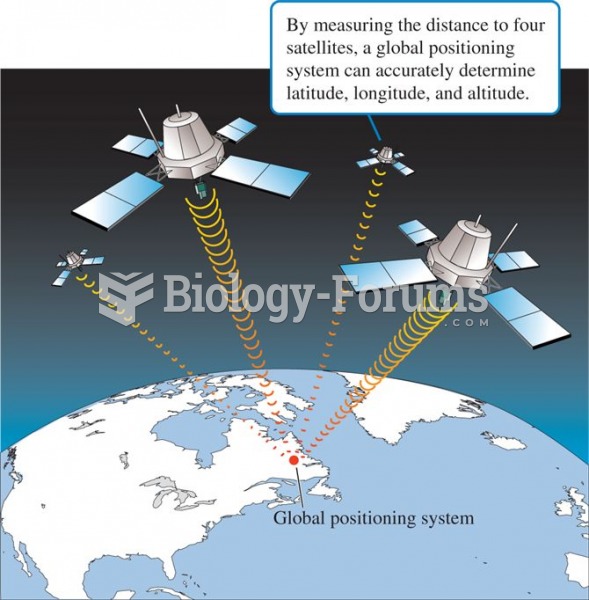 Global positioning systems determine latitude, longitude, and altitude by measuring the distance fro
Global positioning systems determine latitude, longitude, and altitude by measuring the distance fro
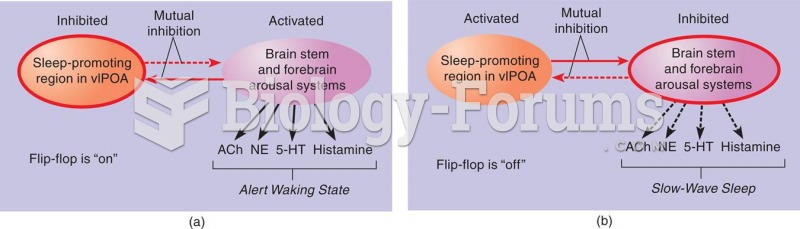 The Sleep/Waking Flip-Flop According to Saper et al. (2001), the major sleep-promoting region (the v
The Sleep/Waking Flip-Flop According to Saper et al. (2001), the major sleep-promoting region (the v