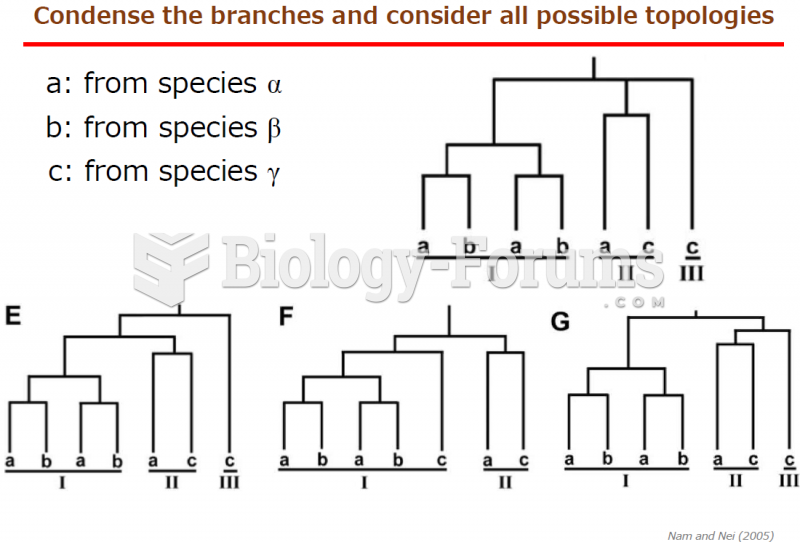
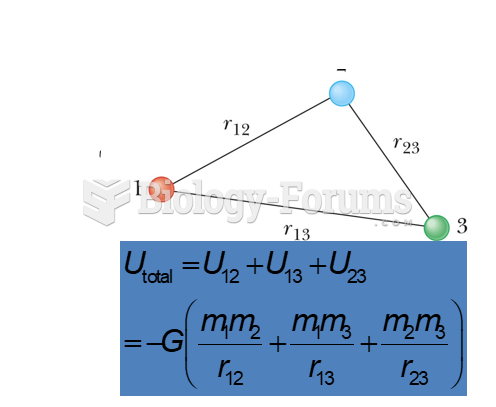
|
|
|
Approximately one in three babies in the United States is now delivered by cesarean section. The number of cesarean sections in the United States has risen 46% since 1996.
Walt Disney helped combat malaria by making an animated film in 1943 called The Winged Scourge. This short film starred the seven dwarfs and taught children that mosquitos transmit malaria, which is a very bad disease. It advocated the killing of mosquitos to stop the disease.
A good example of polar molecules can be understood when trying to make a cake. If water and oil are required, they will not mix together. If you put them into a measuring cup, the oil will rise to the top while the water remains on the bottom.
Pope Sylvester II tried to introduce Arabic numbers into Europe between the years 999 and 1003, but their use did not catch on for a few more centuries, and Roman numerals continued to be the primary number system.
Once thought to have neurofibromatosis, Joseph Merrick (also known as "the elephant man") is now, in retrospect, thought by clinical experts to have had Proteus syndrome. This endocrine disease causes continued and abnormal growth of the bones, muscles, skin, and so on and can become completely debilitating with severe deformities occurring anywhere on the body.