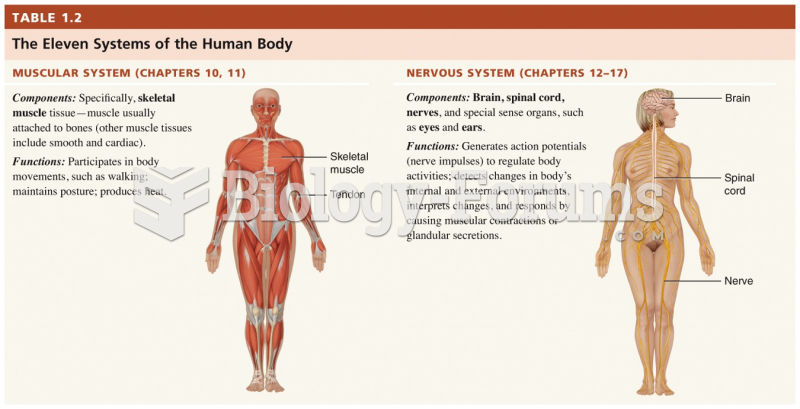
|
|
|
According to the FDA, adverse drug events harmed or killed approximately 1,200,000 people in the United States in the year 2015.
All patients with hyperparathyroidism will develop osteoporosis. The parathyroid glands maintain blood calcium within the normal range. All patients with this disease will continue to lose calcium from their bones every day, and there is no way to prevent the development of osteoporosis as a result.
About 60% of newborn infants in the United States are jaundiced; that is, they look yellow. Kernicterus is a form of brain damage caused by excessive jaundice. When babies begin to be affected by excessive jaundice and begin to have brain damage, they become excessively lethargic.
When blood is exposed to air, it clots. Heparin allows the blood to come in direct contact with air without clotting.
Many people have small pouches in their colons that bulge outward through weak spots. Each pouch is called a diverticulum. About 10% of Americans older than age 40 years have diverticulosis, which, when the pouches become infected or inflamed, is called diverticulitis. The main cause of diverticular disease is a low-fiber diet.