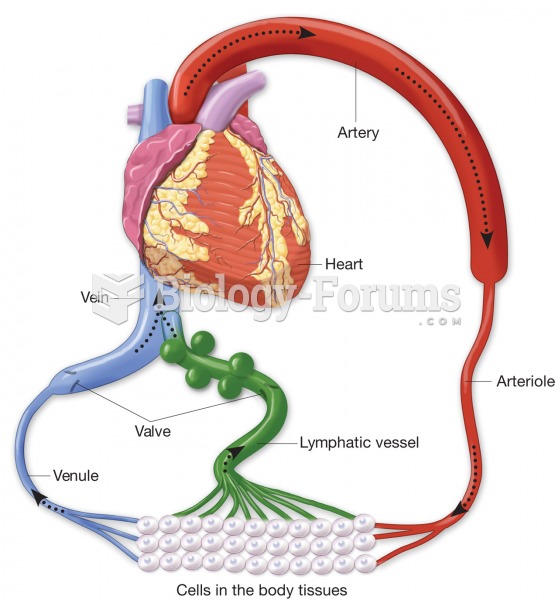
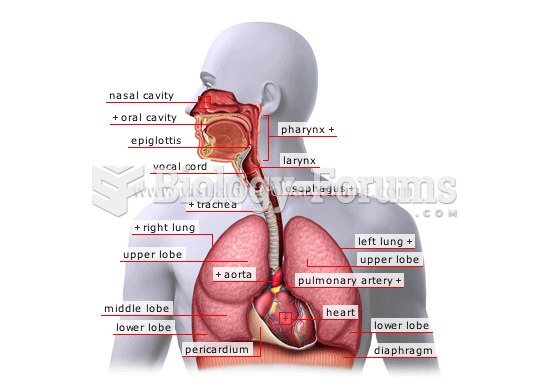
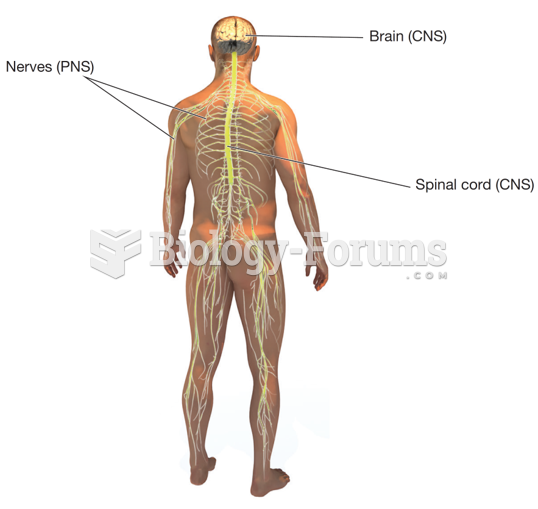
|
|
|
The Centers for Disease Control and Prevention has released reports detailing the deaths of infants (younger than 1 year of age) who died after being given cold and cough medications. This underscores the importance of educating parents that children younger than 2 years of age should never be given over-the-counter cold and cough medications without consulting their physicians.
Most women experience menopause in their 50s. However, in 1994, an Italian woman gave birth to a baby boy when she was 61 years old.
Signs and symptoms that may signify an eye tumor include general blurred vision, bulging eye(s), double vision, a sensation of a foreign body in the eye(s), iris defects, limited ability to move the eyelid(s), limited ability to move the eye(s), pain or discomfort in or around the eyes or eyelids, red or pink eyes, white or cloud spots on the eye(s), colored spots on the eyelid(s), swelling around the eyes, swollen eyelid(s), and general vision loss.
Studies show that systolic blood pressure can be significantly lowered by taking statins. In fact, the higher the patient's baseline blood pressure, the greater the effect of statins on his or her blood pressure.
The top five reasons that children stay home from school are as follows: colds, stomach flu (gastroenteritis), ear infection (otitis media), pink eye (conjunctivitis), and sore throat.