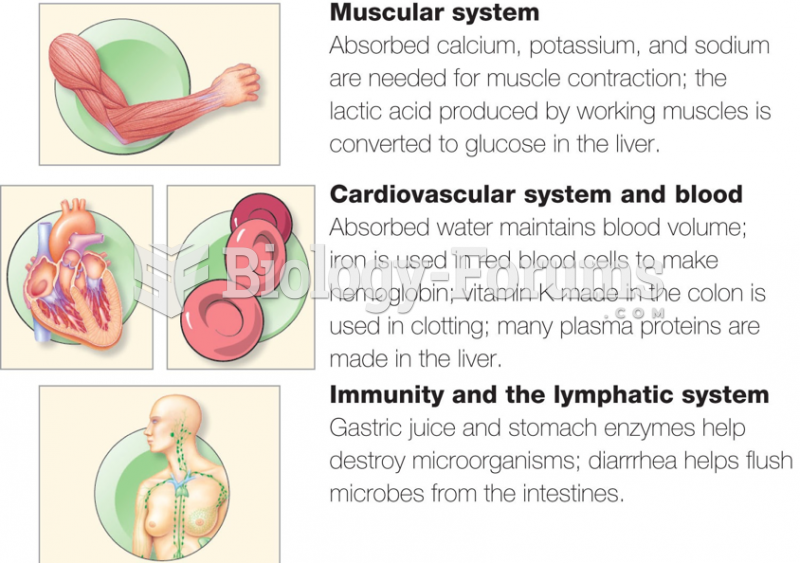
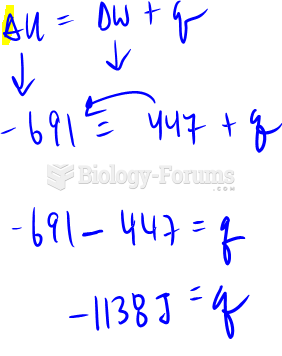
|
|
|
In 2006, a generic antinausea drug named ondansetron was approved. It is used to stop nausea and vomiting associated with surgery, chemotherapy, and radiation therapy.
Oxytocin is recommended only for pregnancies that have a medical reason for inducing labor (such as eclampsia) and is not recommended for elective procedures or for making the birthing process more convenient.
Signs and symptoms of a drug overdose include losing consciousness, fever or sweating, breathing problems, abnormal pulse, and changes in skin color.
Adolescents often feel clumsy during puberty because during this time of development, their hands and feet grow faster than their arms and legs do. The body is therefore out of proportion. One out of five adolescents actually experiences growing pains during this period.
Illicit drug use costs the United States approximately $181 billion every year.