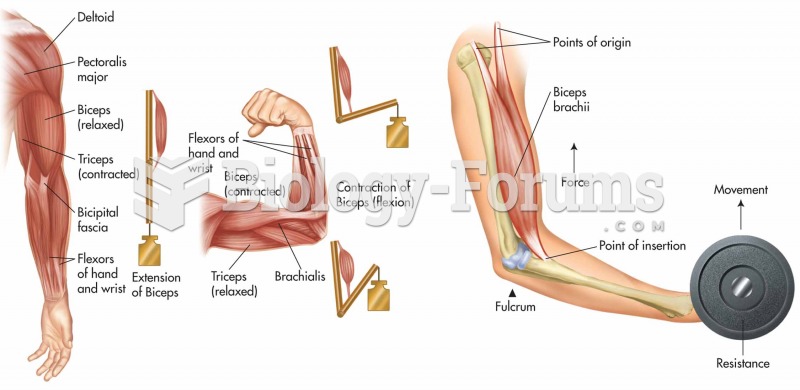
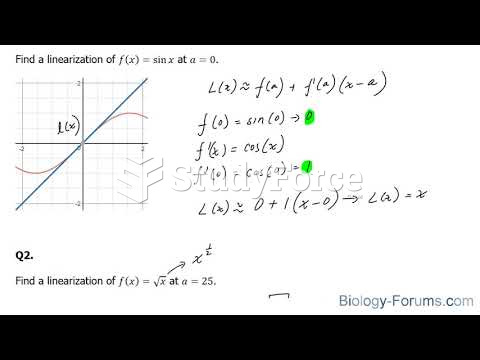
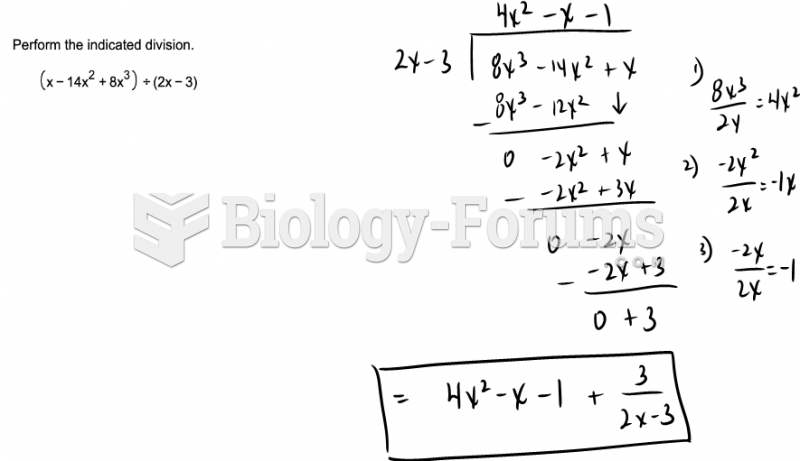
|
|
|
In the United States, congenital cytomegalovirus causes one child to become disabled almost every hour. CMV is the leading preventable viral cause of development disability in newborns. These disabilities include hearing or vision loss, and cerebral palsy.
Many people have small pouches in their colons that bulge outward through weak spots. Each pouch is called a diverticulum. About 10% of Americans older than age 40 years have diverticulosis, which, when the pouches become infected or inflamed, is called diverticulitis. The main cause of diverticular disease is a low-fiber diet.
Multiple experimental evidences have confirmed that at the molecular level, cancer is caused by lesions in cellular DNA.
HIV testing reach is still limited. An estimated 40% of people with HIV (more than 14 million) remain undiagnosed and do not know their infection status.
Today, nearly 8 out of 10 pregnant women living with HIV (about 1.1 million), receive antiretrovirals.