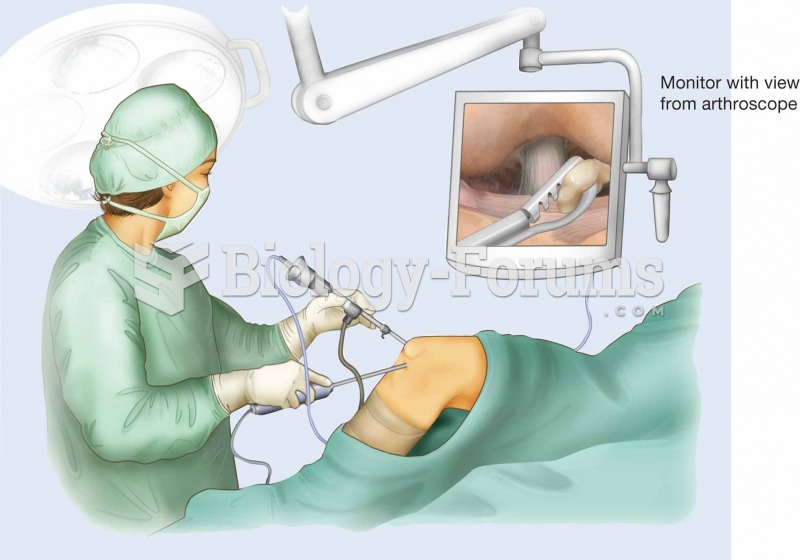
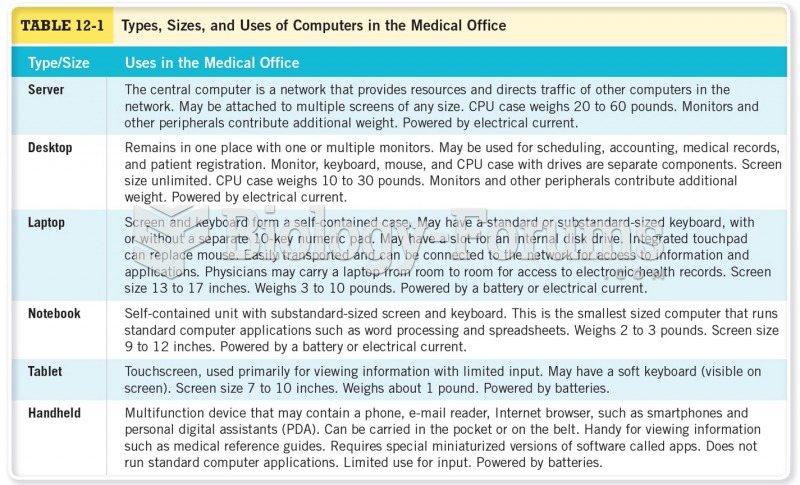
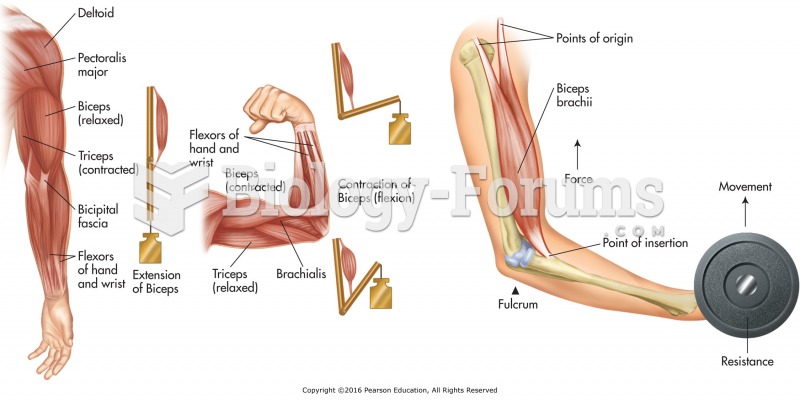
|
|
|
Elderly adults are at greatest risk of stroke and myocardial infarction and have the most to gain from prophylaxis. Patients ages 60 to 80 years with blood pressures above 160/90 mm Hg should benefit from antihypertensive treatment.
Addicts to opiates often avoid treatment because they are afraid of withdrawal. Though unpleasant, with proper management, withdrawal is rarely fatal and passes relatively quickly.
Asthma attacks and symptoms usually get started by specific triggers (such as viruses, allergies, gases, and air particles). You should talk to your doctor about these triggers and find ways to avoid or get rid of them.
One way to reduce acid reflux is to lose two or three pounds. Most people lose weight in the belly area first when they increase exercise, meaning that heartburn can be reduced quickly by this method.
The calories found in one piece of cherry cheesecake could light a 60-watt light bulb for 1.5 hours.