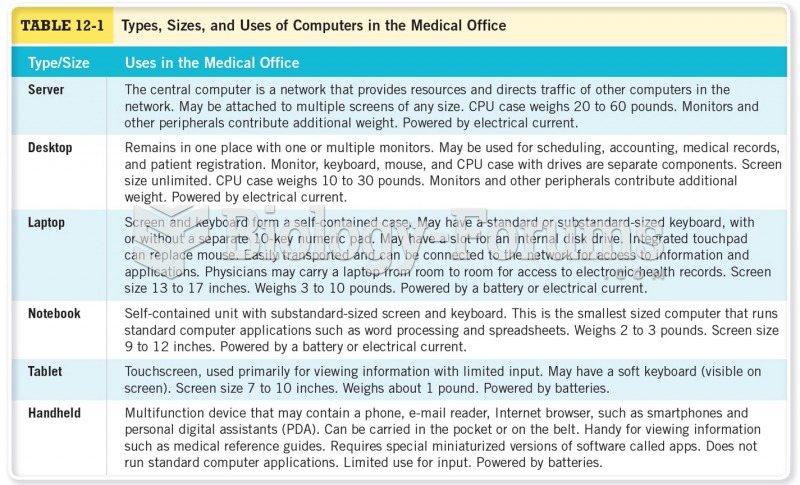
|
|
|
Medication errors are more common among seriously ill patients than with those with minor conditions.
The U.S. Preventive Services Task Force recommends that all women age 65 years of age or older should be screened with bone densitometry.
For about 100 years, scientists thought that peptic ulcers were caused by stress, spicy food, and alcohol. Later, researchers added stomach acid to the list of causes and began treating ulcers with antacids. Now it is known that peptic ulcers are predominantly caused by Helicobacter pylori, a spiral-shaped bacterium that normally exist in the stomach.
In 1885, the Lloyd Manufacturing Company of Albany, New York, promoted and sold "Cocaine Toothache Drops" at 15 cents per bottle! In 1914, the Harrison Narcotic Act brought the sale and distribution of this drug under federal control.
A good example of polar molecules can be understood when trying to make a cake. If water and oil are required, they will not mix together. If you put them into a measuring cup, the oil will rise to the top while the water remains on the bottom.
 Taking a blood pressure is one of the procedures the medical assistant extern may perform under the ...
Taking a blood pressure is one of the procedures the medical assistant extern may perform under the ...
 Walk around the head of the table to the left side and reach across to perform threecount stroking ...
Walk around the head of the table to the left side and reach across to perform threecount stroking ...
 Continuing with one fist, perform effleurage along the iliotibial band and the tensor fascia lata ...
Continuing with one fist, perform effleurage along the iliotibial band and the tensor fascia lata ...