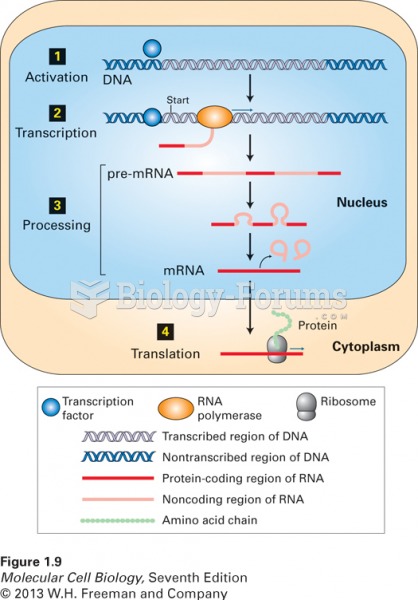
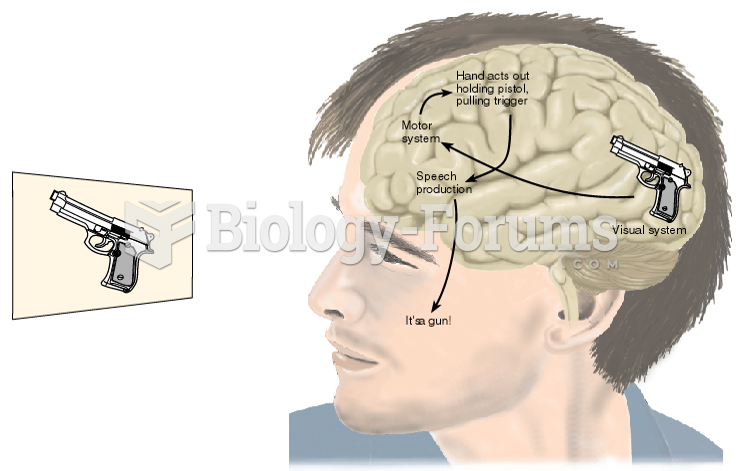
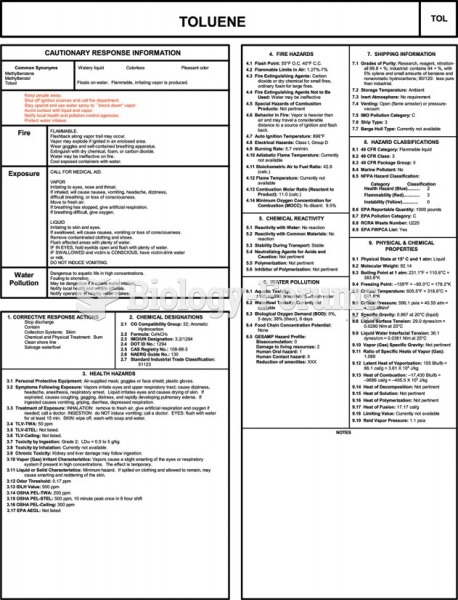
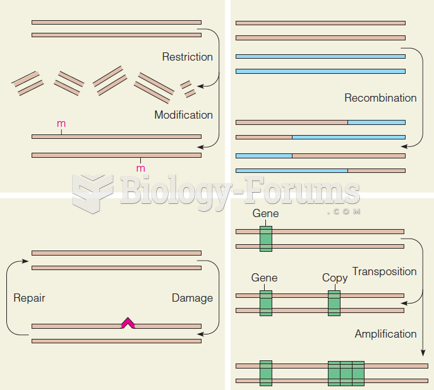
|
|
|
Though Candida and Aspergillus species are the most common fungal pathogens causing invasive fungal disease in the immunocompromised, infections due to previously uncommon hyaline and dematiaceous filamentous fungi are occurring more often today. Rare fungal infections, once accurately diagnosed, may require surgical debridement, immunotherapy, and newer antifungals used singly or in combination with older antifungals, on a case-by-case basis.
Sperm cells are so tiny that 400 to 500 million (400,000,000–500,000,000) of them fit onto 1 tsp.
Human kidneys will clean about 1 million gallons of blood in an average lifetime.
Despite claims by manufacturers, the supplement known as Ginkgo biloba was shown in a study of more than 3,000 participants to be ineffective in reducing development of dementia and Alzheimer’s disease in older people.
About 3% of all pregnant women will give birth to twins, which is an increase in rate of nearly 60% since the early 1980s.