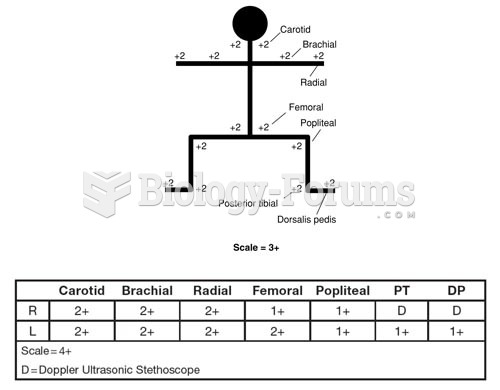
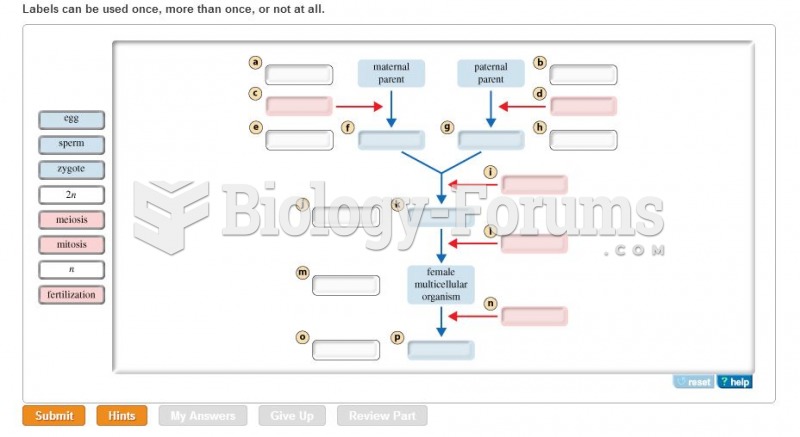
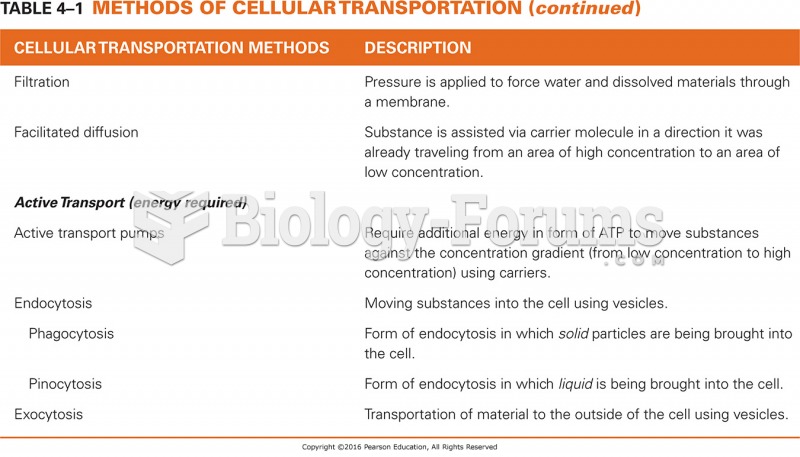
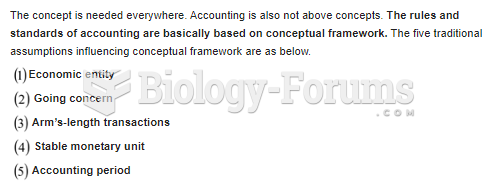
|
|
|
Always store hazardous household chemicals in their original containers out of reach of children. These include bleach, paint, strippers and products containing turpentine, garden chemicals, oven cleaners, fondue fuels, nail polish, and nail polish remover.
There are actually 60 minerals, 16 vitamins, 12 essential amino acids, and three essential fatty acids that your body needs every day.
The oldest recorded age was 122. Madame Jeanne Calment was born in France in 1875 and died in 1997. She was a vegetarian and loved olive oil, port wine, and chocolate.
There are approximately 3 million unintended pregnancies in the United States each year.
Alzheimer's disease affects only about 10% of people older than 65 years of age. Most forms of decreased mental function and dementia are caused by disuse (letting the mind get lazy).