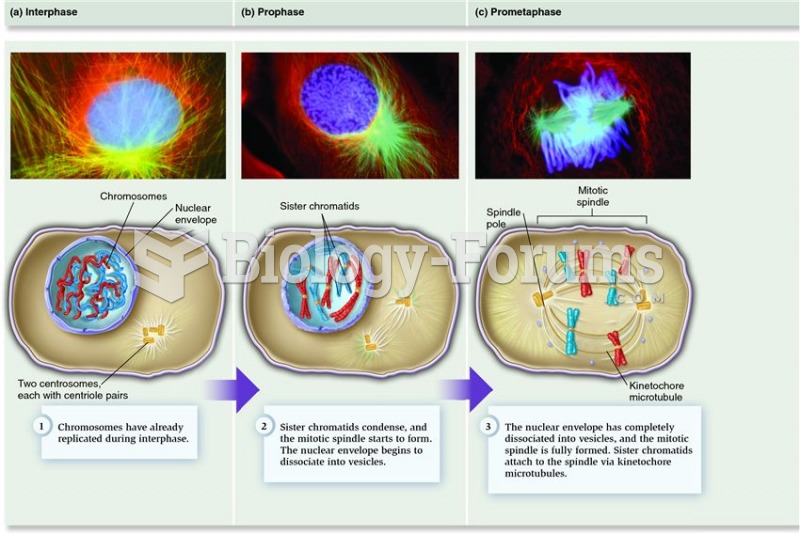
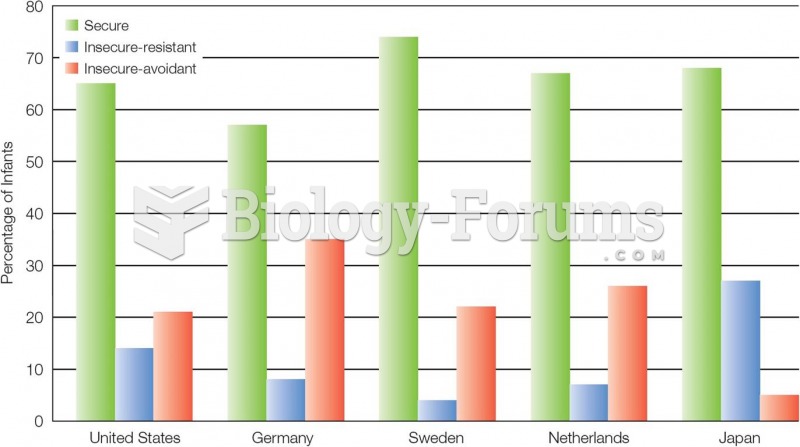
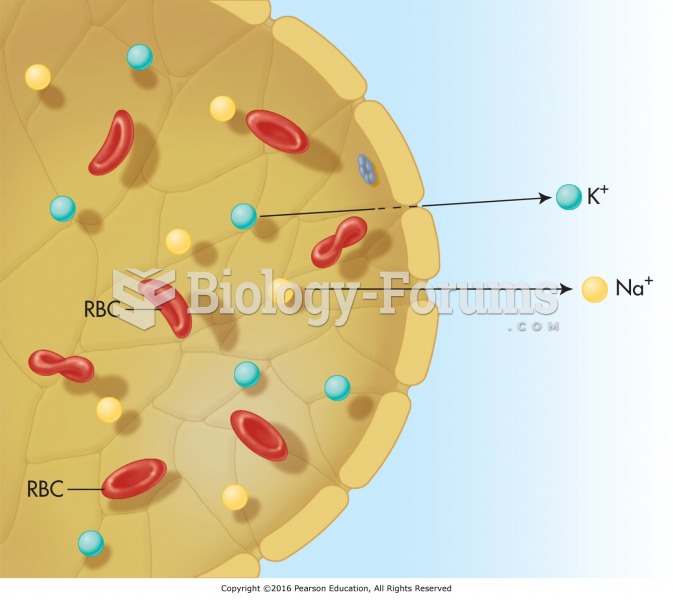
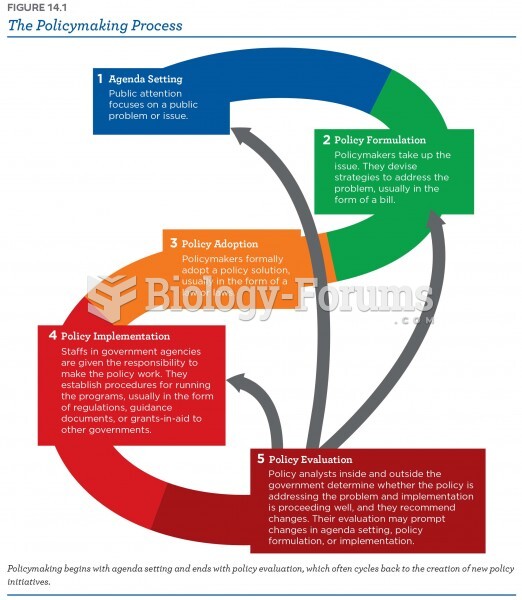
|
|
|
According to the Migraine Research Foundation, migraines are the third most prevalent illness in the world. Women are most affected (18%), followed by children of both sexes (10%), and men (6%).
Over time, chronic hepatitis B virus and hepatitis C virus infections can progress to advanced liver disease, liver failure, and hepatocellular carcinoma. Unlike other forms, more than 80% of hepatitis C infections become chronic and lead to liver disease. When combined with hepatitis B, hepatitis C now accounts for 75% percent of all cases of liver disease around the world. Liver failure caused by hepatitis C is now leading cause of liver transplants in the United States.
Colchicine is a highly poisonous alkaloid originally extracted from a type of saffron plant that is used mainly to treat gout.
The first-known contraceptive was crocodile dung, used in Egypt in 2000 BC. Condoms were also reportedly used, made of animal bladders or intestines.
In ancient Rome, many of the richer people in the population had lead-induced gout. The reason for this is unclear. Lead poisoning has also been linked to madness.