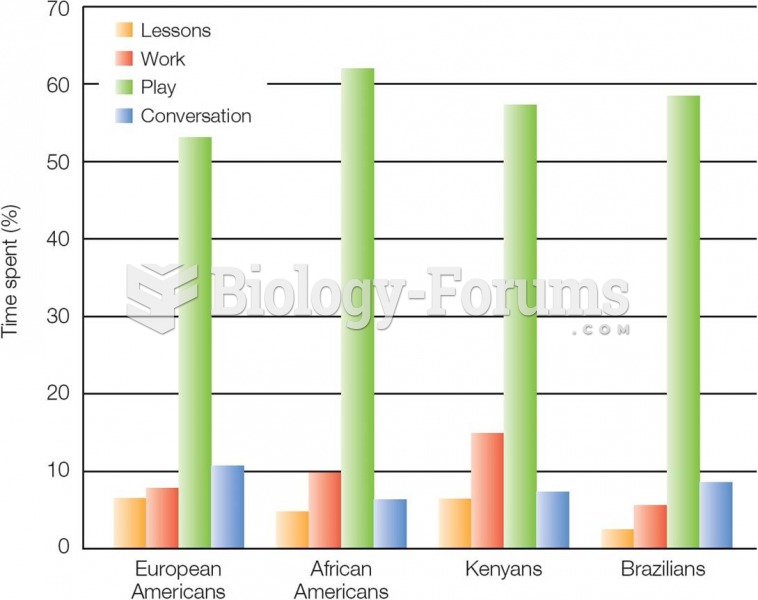
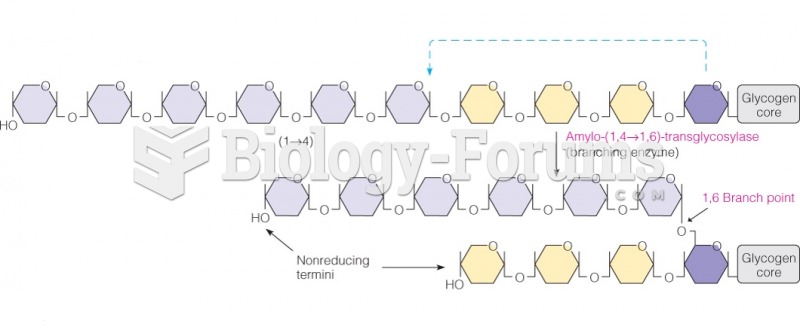
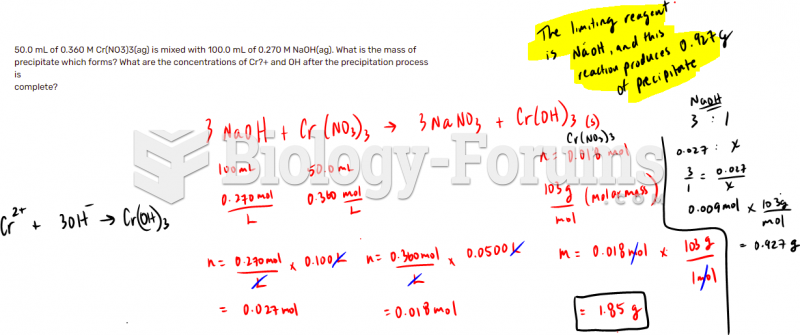
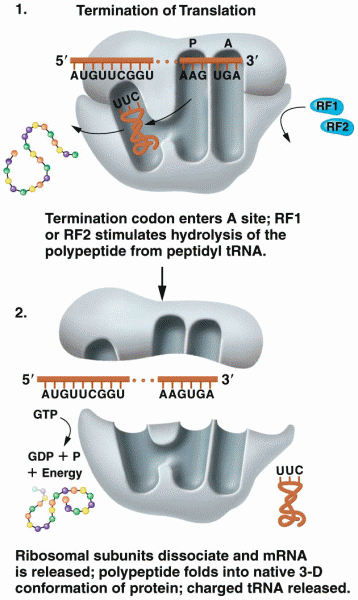
|
|
|
The average older adult in the United States takes five prescription drugs per day. Half of these drugs contain a sedative. Alcohol should therefore be avoided by most senior citizens because of the dangerous interactions between alcohol and sedatives.
Interferon was scarce and expensive until 1980, when the interferon gene was inserted into bacteria using recombinant DNA technology, allowing for mass cultivation and purification from bacterial cultures.
Vaccines prevent between 2.5 and 4 million deaths every year.
Malaria was not eliminated in the United States until 1951. The term eliminated means that no new cases arise in a country for 3 years.
Patients who have been on total parenteral nutrition for more than a few days may need to have foods gradually reintroduced to give the digestive tract time to start working again.