|
|
|
Cucumber slices relieve headaches by tightening blood vessels, reducing blood flow to the area, and relieving pressure.
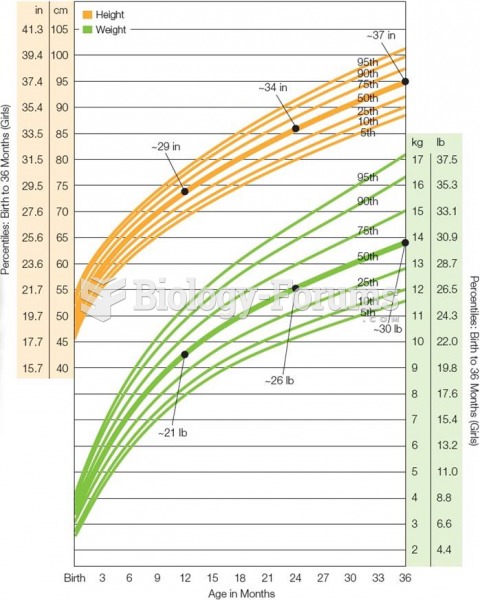
Hip fractures are the most serious consequences of osteoporosis. The incidence of hip fractures increases with each decade among patients in their 60s to patients in their 90s for both women and men of all populations. Men and women older than 80 years of age show the highest incidence of hip fractures.
When taking monoamine oxidase inhibitors, people should avoid a variety of foods, which include alcoholic beverages, bean curd, broad (fava) bean pods, cheese, fish, ginseng, protein extracts, meat, sauerkraut, shrimp paste, soups, and yeast.
Pink eye is a term that refers to conjunctivitis, which is inflammation of the thin, clear membrane (conjunctiva) over the white part of the eye (sclera). It may be triggered by a virus, bacteria, or foreign body in the eye. Antibiotic eye drops alleviate bacterial conjunctivitis, and antihistamine allergy pills or eye drops help control allergic conjunctivitis symptoms.
There are immediate benefits of chiropractic adjustments that are visible via magnetic resonance imaging (MRI). It shows that spinal manipulation therapy is effective in decreasing pain and increasing the gaps between the vertebrae, reducing pressure that leads to pain.