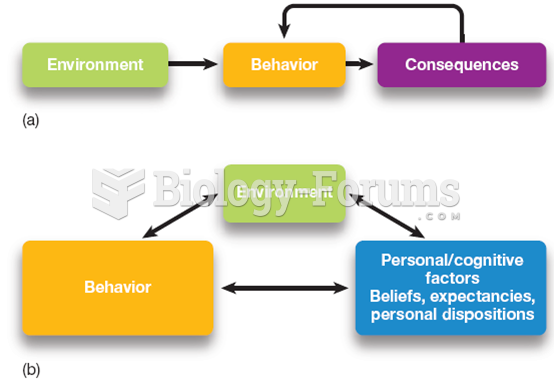
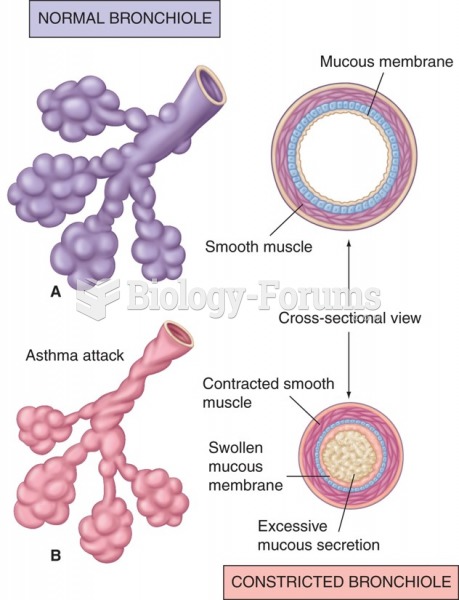
|
|
|
Your heart beats over 36 million times a year.
Not getting enough sleep can greatly weaken the immune system. Lack of sleep makes you more likely to catch a cold, or more difficult to fight off an infection.
Women are two-thirds more likely than men to develop irritable bowel syndrome. This may be attributable to hormonal changes related to their menstrual cycles.
The human body produces and destroys 15 million blood cells every second.
A strange skin disease referred to as Morgellons has occurred in the southern United States and in California. Symptoms include slowly healing sores, joint pain, persistent fatigue, and a sensation of things crawling through the skin. Another symptom is strange-looking, threadlike extrusions coming out of the skin.