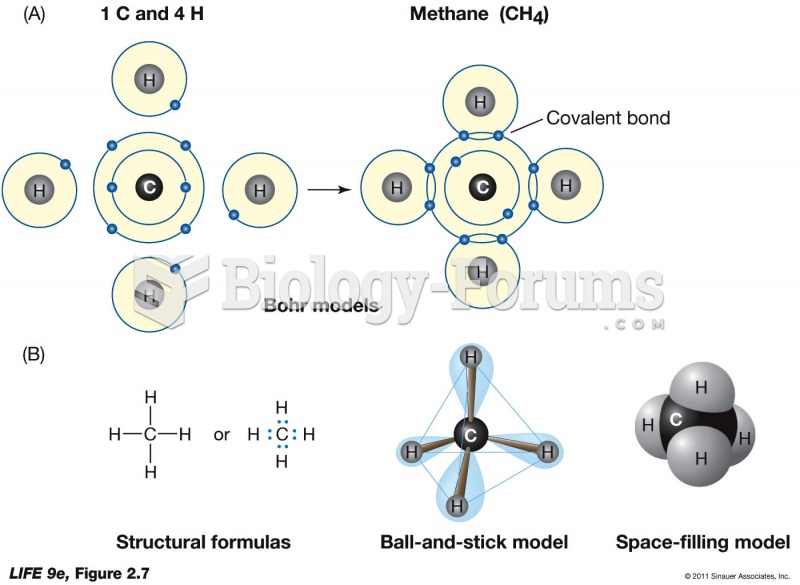
|
|
|
Giardia is one of the most common intestinal parasites worldwide, and infects up to 20% of the world population, mostly in poorer countries with inadequate sanitation. Infections are most common in children, though chronic Giardia is more common in adults.
If you use artificial sweeteners, such as cyclamates, your eyes may be more sensitive to light. Other factors that will make your eyes more sensitive to light include use of antibiotics, oral contraceptives, hypertension medications, diuretics, and antidiabetic medications.
In ancient Rome, many of the richer people in the population had lead-induced gout. The reason for this is unclear. Lead poisoning has also been linked to madness.
It is important to read food labels and choose foods with low cholesterol and saturated trans fat. You should limit saturated fat to no higher than 6% of daily calories.
More than one-third of adult Americans are obese. Diseases that kill the largest number of people annually, such as heart disease, cancer, diabetes, stroke, and hypertension, can be attributed to diet.