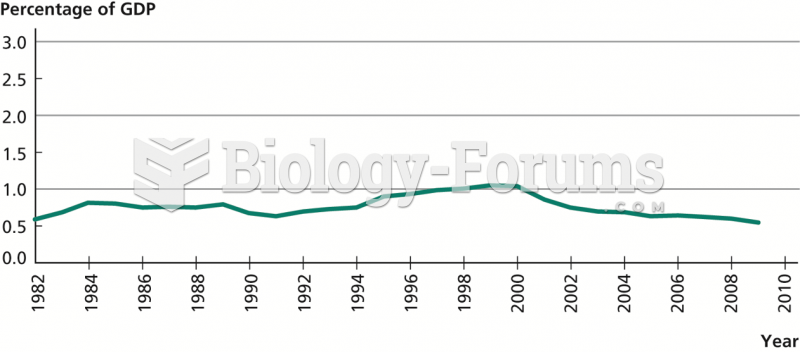
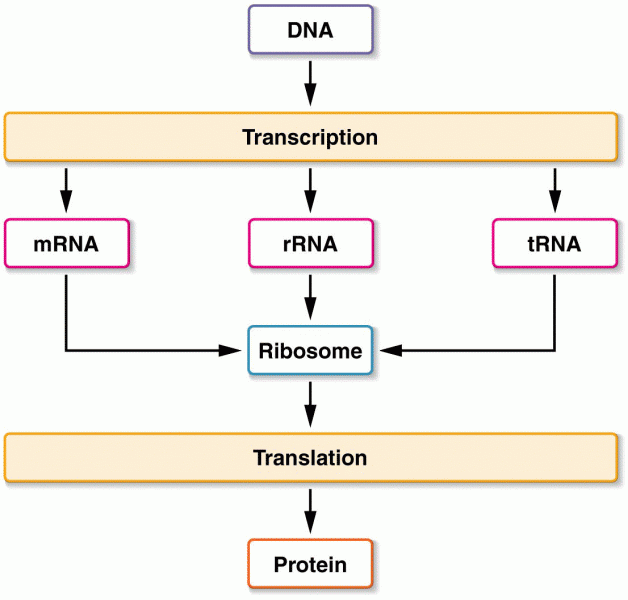
|
|
|
In 2012, nearly 24 milliion Americans, aged 12 and older, had abused an illicit drug, according to the National Institute on Drug Abuse (NIDA).
According to research, pregnant women tend to eat more if carrying a baby boy. Male fetuses may secrete a chemical that stimulates their mothers to step up her energy intake.
As of mid-2016, 18.2 million people were receiving advanced retroviral therapy (ART) worldwide. This represents between 43–50% of the 34–39.8 million people living with HIV.
Many of the drugs used by neuroscientists are derived from toxic plants and venomous animals (such as snakes, spiders, snails, and puffer fish).
A strange skin disease referred to as Morgellons has occurred in the southern United States and in California. Symptoms include slowly healing sores, joint pain, persistent fatigue, and a sensation of things crawling through the skin. Another symptom is strange-looking, threadlike extrusions coming out of the skin.